EzRSA
题目
1 | from Crypto.Util.number import * |
题解
首先e等于3,直接开方可解
1 | from Crypto.Util.number import * |
预期解法为,通过hint2可以求出一个kMod,然后在kMod的环下,求出移位后的m
然后继续构造在mod n下的环,求出真正的m
1 | from Crypto.Util.number import * |
FunnyEncrypt
题目
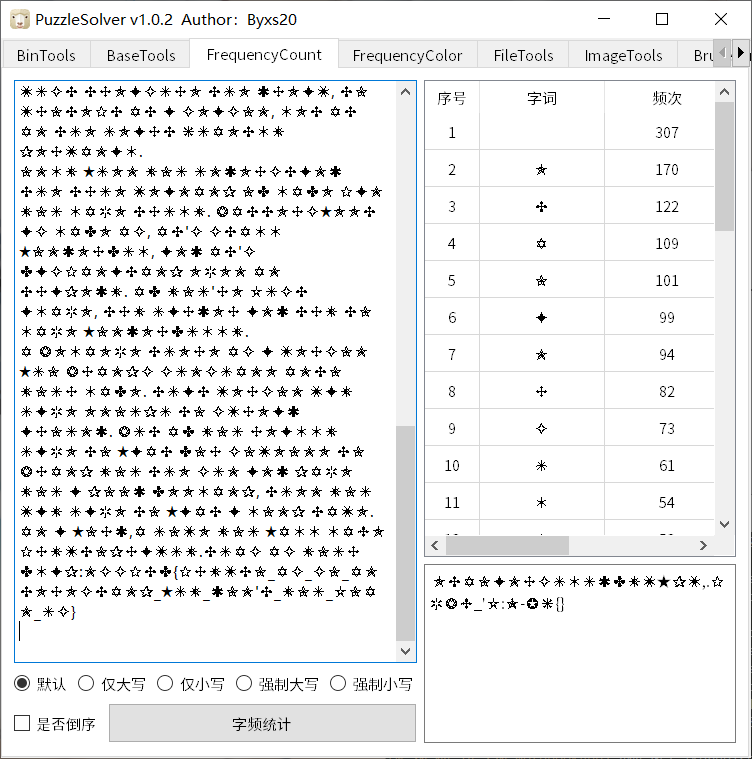
1 | ✧✡✭ |
题解
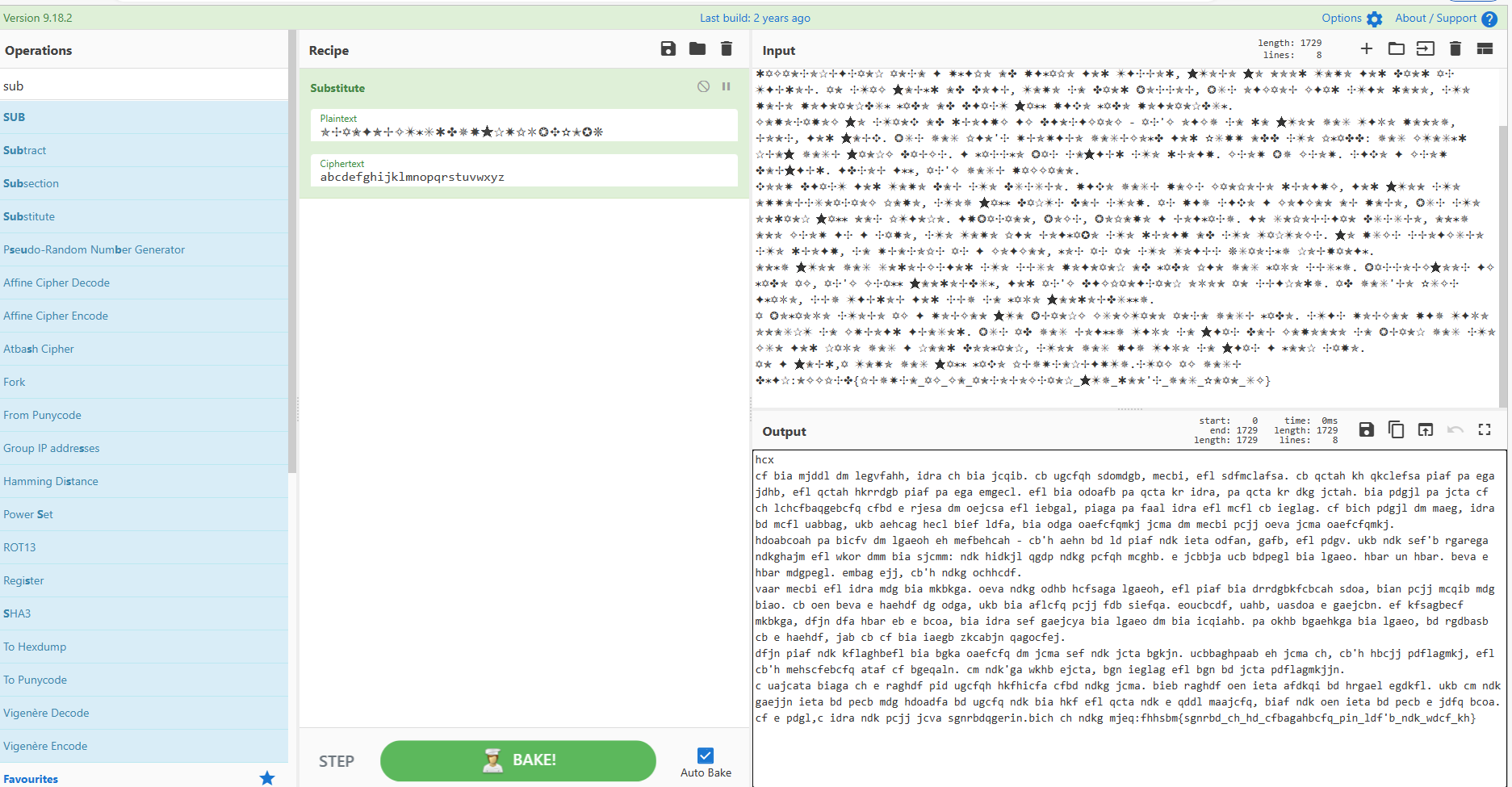
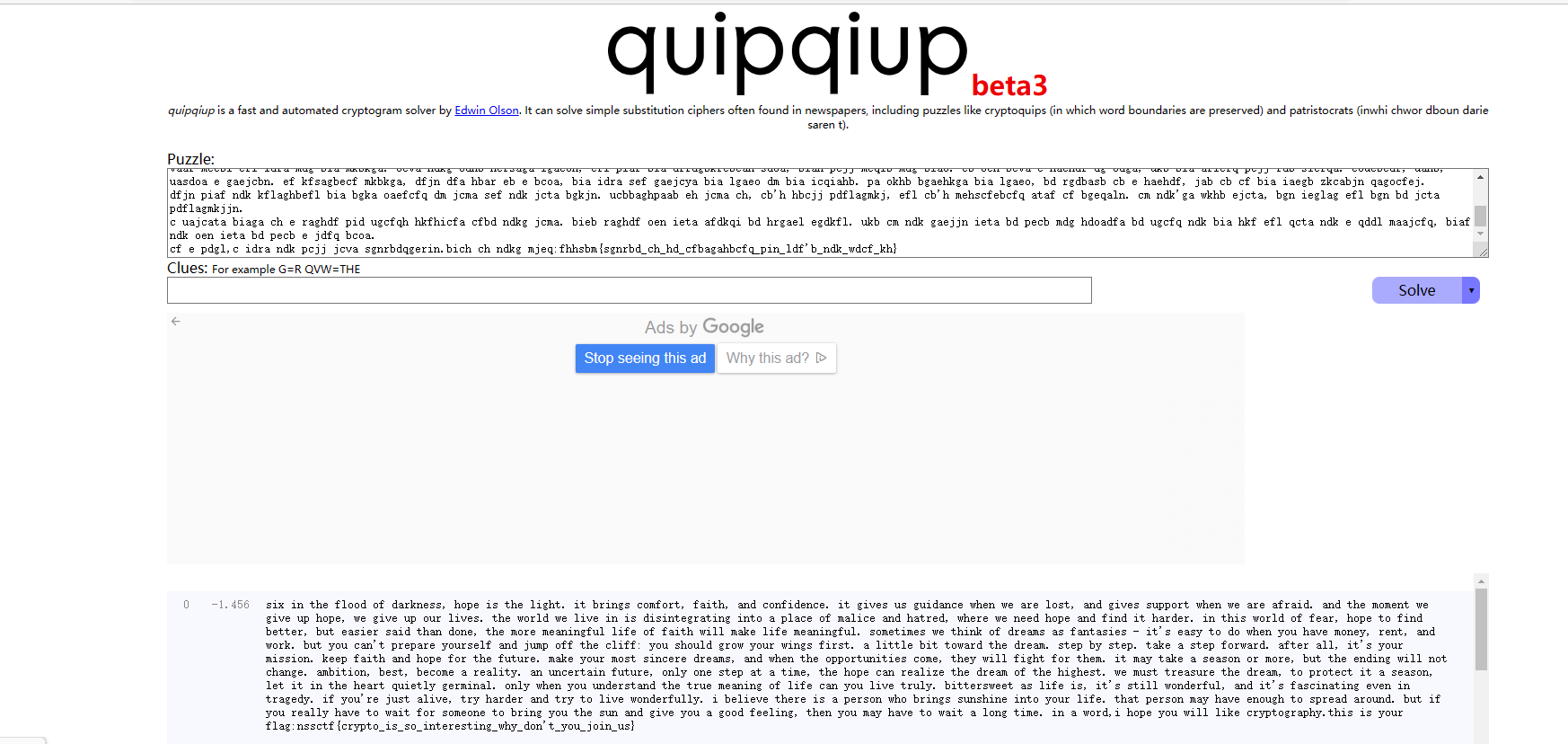
先统计各字符数量,从高到低换表,最后用词频分析解密
Math
题目
1 | from secret import flag |
题解
flag分为了两部分,第一部分是已知phi,p和q逆元,直接用脚本分解得p和q
参考链接:write-up/2019/HITCON/Lost_Modulus_Again at master · pcw109550/write-up (github.com)
1 | import gmpy2 |
第二部分分析
1 | from Crypto.Util.number import * |
LatticeLCG
题目
1 | from Crypto.Util.number import * |
题解
代码结构简单,主要通过多组out和e来求出n
求出n后,通过共模攻击求出a,最后利用两组output求b
求n
1 | es = [297332330847212015073434001239859795661, 247136911662054641479463124065475615181, 269964458627145370722389742095701827701, 270745917671094194052444327351021588037, 254010082507930275771798119457499420531, 219178601856077385518322602059961601013, 226562702503988968288128483964146379529, 236756812424464516919183114495913408541, 330800121752029915693039296018980956519, 244800084005240595691424199440981715431, 171753849214889522920105847094773384191, 175843874533972361422410968920873382741, 326554577162848075059517044795930784993, 181842368629269753698222635712342485771, 221634122983362091660188171985742369561, 314244561819808202322467576330355199409, 286703236198397527318161582654787197007, 298101543059628501506668748374542117409, 304158884506393754601331945634109778837, 227577031261920314010408499530794497453] |
共模攻击求a
1 | import gmpy2 |
最后求b,也就是flag
1 | from Crypto.Util.number import * |